Managing network threats: Using Wifi securely and efficiently at home and on the move
The use of Wifi has become standard thanks to the convenience it offers. Browsing while sitting in the garden, checking your e-mails on the move or exploring an unknown city via Google Maps in the hotel – not so long ago these activities we take for granted, weren’t possible. However, with people caught up in the buzz of this new found freedom, they often neglect to treat their wireless network connections with adequate care, leaving out a virtual welcome mat for hackers.
Did you know, that in many networks when you visit various websites it’s possible for all sent data to be logged? Not only does this danger exist on third-party Wifi networks, but even your own wireless network can be at risk without the appropriate protection. Weak encryption, for example, can quickly lead to the abuse of your connection by others to spy on your data or undertake other illegal activities. You needn’t sacrifice the convenience of Wifi though, as we will explain how to avoid the greatest risks and use both public hotspots and your own Wifi network securely.
Securing your home network against intruders
The reception range of your Wifi network generally reaches beyond your own home. Most people are aware of this in principle, yet in some ways it’s a concept that’s so abstract it tends to be overlooked. An intruder can easily penetrate an open or insufficiently secured Wifi network from the outside. Using a so-called “sniffer” they can then intercept your Internet traffic and capture data including login details for forums, online stores or even online banking. It’s also possible for an intruder to use your connection to engage in criminal activity such as illegal downloads, spamming or even attacking websites. Your Internet connection can be traced back to you due to your unique IP address, and a potential lawsuit may be the unpleasant result.
It is therefore imperative to prevent strangers from gaining access to your network. In order to accomplish this it is necessary to use good encryption. Up until a few years ago, WEP was the encryption method that was enabled by default in routers. Today WEP is considered very outdated and it’s ESSENTIAL to use WPA or preferably WPA2 with a sufficiently long password. WPA stands for “Wifi Protected Access” and is a common security protocol for wireless networks that relies on the highly secure Advanced Encryption Standard (AES). As dictionary attacks are the only feasible method of breaking this encryption, your password should consist of at least 15 to 20 characters (letters, numbers and also special characters) so it is difficult to crack by current standards. To learn the exact steps to take to enable WPA2 in your router, please refer to the device’s manual.
Alarming news: Court rulings in recent years have demonstrated that the use of outdated WEP encryption is legally considered to be equivalent to using no encryption at all. Several hotspot providers have been convicted of illegal data transfers committed by third parties.
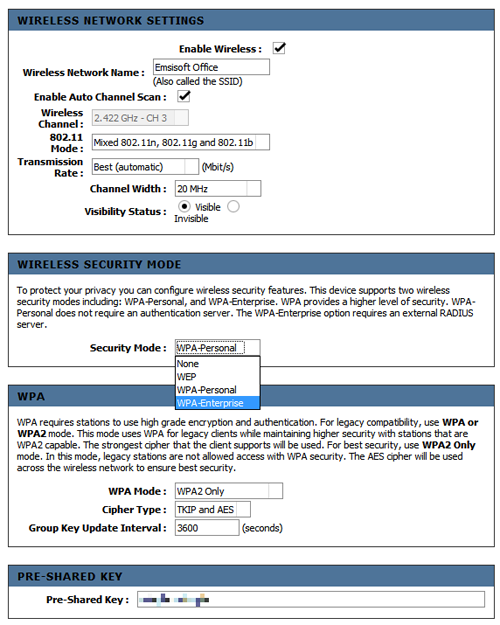
Setting up Wifi encryption in an modern router. WPA2 with the longest possible password protects your network from unwanted guests.
As a rule, routers are usually protected by their own default password. Please avoid the use of default factory settings though and instead use your own strong password. Although with newer devices, it isn’t possible to configure the router from the outside (only via a locally connected cable), applying a strong password provides another layer of protection. You should also keep the router’s firmware up-to-date to ensure that newly discovered vulnerabilities are closed immediately. There have been some high profile cases of vulnerabilities involving well-known router manufacturers in recent years.
If you want to go one step further, you can additionally disable automatic broadcasting of your SSID, which is your network’s name. In the screenshot above, this would be possible via the option “Invisible”. However this can complicate the connection setup for some devices as all data must be entered manually. This measure is purely optional as enabling WPA2 encryption with a strong password and keeping your router up-to-date is generally sufficient to secure your home Wifi network.
You shouldn’t overlook the social aspect of Wifi either though. For example, do you often have people visiting that you only know vaguely, but who wish to use your Wifi briefly? Whether they are your children’s friends, couchsurfing guests or someone else entirely, it’s a sensible idea to change your WPA password regularly.
Using Wifi securely on the move

The success of Wifi has extended beyond the home. Wireless networks have also become a staple in our outside lives. Whether it be in a hotel, a restaurant or a public hotspot in a park – Wifi networks have become a standard almost everywhere. Many people believe they are secure in password protected networks, but this is a fatal misconception.
In general, you are seldom alone on a public network. Other users typically also have access and are sharing the network with you. If you visit unsecured websites, your data can be intercepted by others. Therefore the same risk exists as if you don’t encrypt your home network. Instant messages, e-mail and login details that are sent unencrypted, can thus be logged. Your co-surfers don’t even need to be seasoned hackers; normal sniffer tools are readily available online and will do the job.
It’s important to note that encryption of the network itself only secures access to the network and doesn’t mean that the actual data within the network is encrypted. This is basically like a master key for a high-rise apartment building. All tenants are able to open the common entrance door in the same way as you can log on to a public Wifi hotspot using the corresponding access details. However, much like every tenant also has a unique key that controls access to their own apartment, you must also secure the transmission of your own data.
This is ensured via TLS or SSL encryption. TLS stands for “Transport Layer Security” and is the successor of SSL (Secure Sockets Layer). This may sound complicated, but it’s simply the name for secure data transmission. All current browsers can “handle” TLS or SSL, which enables you to easily and securely visit websites. What can be an an issue however is that even if your browser supports TLS/SSL, this service must be offered by the corresponding website. In reality, this isn’t always the case.
When visiting a website where you enter your personal information, such as Facebook, an online store or your online banking platform, this should ALWAYS occur via HTTPS. This is short for “HyperText Transfer Protocol Secure”, i.e. a secured “http://” connection which is based on TLS/SSL (https://). If the website you are visiting doesn’t support this, then you should refrain from entering any personal details.
Why aren’t all websites available via HTTPS?
Before you become motivated to contact the operators of all unsecured websites, it should be noted that encryption isn’t necessary for the mere retrieval of information. It is essentially much more complex and expensive to offer TLS/SSL on a webserver than it is to use simple, non-encrypted HTTP. Moreover, such a widespread use of encryption would have a negative impact on the Internet infrastructure. In particular, the use of data caching would become complicated and there would be a massive rise in the volume of globally transferred data as a result.
![]()
Emsisoft Licence Center is accessed via a secure connection in Internet Explorer, which is identified by “https” and the symbol on the right-hand side next to the magnifying glass.
How to recognize a secure website
In most browsers, a secure connection can be recognized by the presence of “https://” in the URL as well a symbol, e.g. a small padlock in Internet Explorer. In addition, it must be ensured that the website has a valid certificate that hasn’t been revoked. Fortunately, certificate validation is performed automatically by the browser; in the event that you see a warning or an invalid certificate, you should refrain from transmitting any sensitive information regardless of the presence of “https” or the encryption symbol in the address bar.
If everything is in order, however, you can surf relatively safely. TLS/SSL can also be used for Internet activity outside of the browser, such as in your e-mail software. Unfortunately the use of TLS/SSL for sending e-mail isn’t always as straightforward. Although many e-mail providers support TLS or SSL and it can be enabled in your e-mail client’s settings, some Internet providers throw a spanner in the works by blocking commonly encrypted POP3 or SMPT ports. Under these circumstances, sending e-mails securely is only possible via a https webmail interface, an alternative port offered by the mail server or by using a VPN.
Additional security measures for using Wifi
A firewall can be a sensible addition when surfing on third-party Wifi networks because even if you transfer all important data via encrypted connections, your PC itself can still be reached by others within the network. Open ports or vulnerabilities in programs may enable intruders to gain control of your OS. It’s even more important to ensure that you don’t have any open file shares as all users of the same hotspot have access to shared files or printers unless they are protected by a password.

You may also wish to take your security a step further when on the move. The magic word is VPN: Virtual Private Network. This requires the use of either Windows built-in PPTP or third-party software such as the freely available
OpenVPN. After installation, you connect to your wireless network in the same way as usual, but the VPN client establishes a secure connection between your PC and the VPN server on the Internet. This secure connection then works like a tunnel through which your data is transferred relatively safely.
We limit ourselves to saying “relatively” for the simple reason that unfortunately there is always room for weak spots in computer security. Obviously, you should ensure that the VPN you use is secure and trustworthy. The potential always exists for your traffic to be intercepted at or behind the VPN server, so you have to rely on the integrity of your provider and trust that they don’t have illegal intentions. Please be vigilant and use caution when choosing your VPN provider.
Have a nice (malware-free) day!
Your Emsisoft Team
www.emsisoft.com


