Scan types
(can be combined)
/f=[path], /files=[path]
Scans specified disks, folders or files for malware infections. Folder paths must be enclosed in quotation marks. Multiple paths need to be delimited by commas.
Example: a2cmd /f="c:\windows\","c:\program files\"
/quick
Abbreviation for running a quick system check. Scans all active programs and malware traces (registry, files).
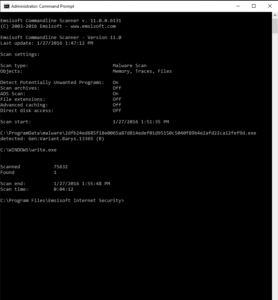
/malware
Scans all places that Malware typically infects. A Malware Scan is the best choice for most users. It’s fast and thoroughly examines all known areas of the device where active malware typically resides.
/m, /memory
Scans all active programs.
/t, /traces
Scans the registry and the file/folder structures on a hard disk for malware traces.
/fh=[handle], /pid=[PID]
Scan a file by handle. Requires the ID of the process that keeps the handle.
/b=[pointer] /bs=[size] /pid=[PID]
Scan a data buffer in memory. Requires the buffer size and the ID of the process that keeps the buffer.
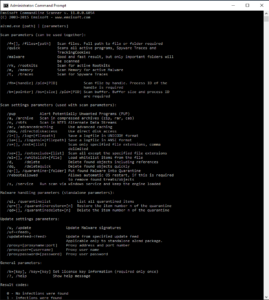
Scan settings
(for precise adjustment of the scan types)
/pup
Also detects Potentially Unwanted Programs (programs that are not specifically malicious but are often installed without user consent)
/a, /archive
Scans also within archive files such as ZIP, RAR, CAB, and self-extracting archives.
/n, /ntfs
Scans also hidden data flows in NTFS disks.
/ac, /advancedcaching
Uses the advanced caching to avoid unnecessary re-scans.
/l=[path], /log=[path]
Saves a scan log to the specified file. The text-based log is saved in Unicode format.
Example: a2cmd /malware /log="c:\scans\scan.log"
/la=[path], /logansi=[path]
Same as the /l bzw /log parameter, but the log is saved in ANSI Format.
/wl=[path], /whitelist=[path]
Uses the specified whitelist file for excluding certain files, folders or malware names in the scan. Whitelist files must be text files where each line is one of the items to be excluded.
Example: a2cmd /f="c:\" /wl="c:\whitelist.txt"
/d, /delete
Deletes all detected malware objects at once during the scan. Also deletes references to the detected file, e.g. autorun entries in the registry.
/dq, /deletequick
Deletes all detected malware objects at once during the scan. Only the detected file itself is deleted. Quicker than /d or /delete.
/q=[folder], /quarantine=[folder]
Immediately place detected malware in quarantine during the scan. The quarantine folder can be specified. Detected objects are saved and encrypted there so that they cannot cause further damage.
/s, /service
Defines if the Anti-Malware service is to be used for scanning.
Background: When running many short scans, loading the scan engine afresh at each start of a2cmd is inefficient. Using the /s or /service parameter makes the Anti-Malware service load the engine and keep it loaded for later scans. If the service is not yet started or installed it is installed and started when the service parameter is run for the first time. This command is not available in Emsisoft Remediation Kit because the service component is not included.
Malware handling
(to be used alone)
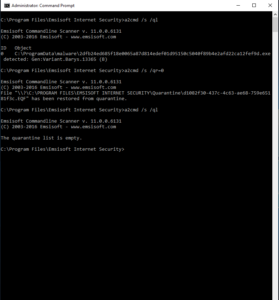
/ql, /quarantinelist
Lists all objects that are under quarantine. The consecutive number at the beginning of each line can be used for deleting or restoring (zero-based index).
/qr=[n], /quarantinerestore=[n]
Restores an object under quarantine with the specified index number. If no number is specified, all objects are restored.
Example: a2cmd /qr=0
/qd=[n], /quarantinedelete=[n]
Deletes an object under quarantine with the specified index number.
Online updates
(to be used alone)
/u, /update
Must be used alone. Runs an online update of all program components and signatures. If a2cmd is used as a part of Emsisoft Anti-Malware, this command triggers an update of the whole Emsisoft Anti-Malware package.
/uf=[feed], /updatefeed=[feed]
Update from specified update feed
Applicable only to standalone a2cmd package
/proxy=[proxyname:port]
Sets a proxy host and port number to be used for connections to the update server.
/proxyuser=[username]
Sets a proxy username if the proxy requires authentication.
/proxypassword=[password]
Sets a proxy password if the proxy requires authentication.
General commands
(to be used alone)
/k=[key], /key=[key]
Set license key information (required only once)
/?, /help
Shows an overview of all available parameters.
Result codes
0 – No infections were found
1 – Infections were found