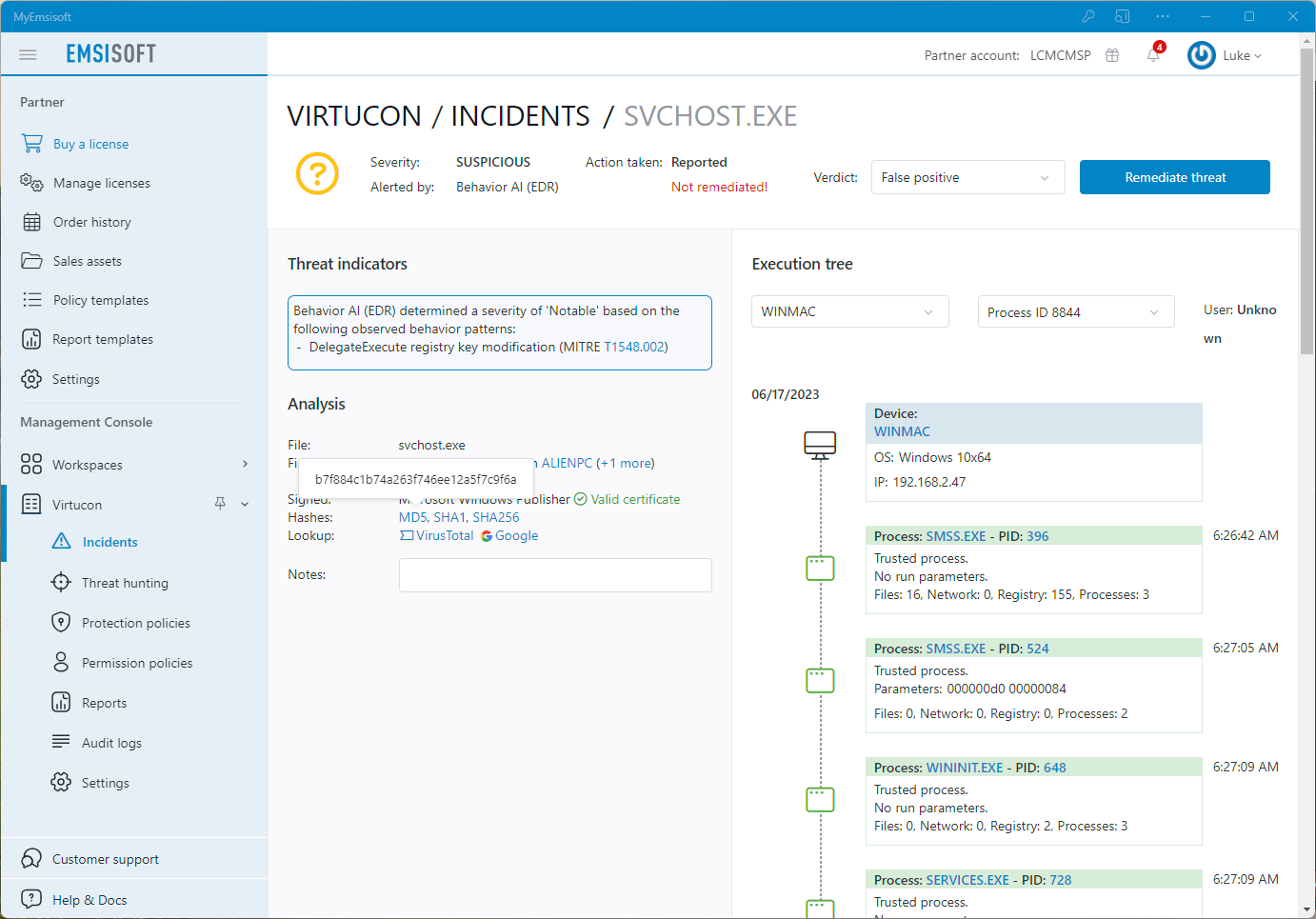
Web filtering – host based
Web Protection cuts cyberthreats off at the source by blocking connections to dangerous hosts.
Emsisoft achieves this by maintaining a huge database of malicious hostnames and IPs gathered from publicly available lists, insider intel, and verified user submissions. Web Protection is host-based and works at the Windows system level, which means it works with all browsers and almost all programs, and doesn’t require updates when new browser versions are released.