New in 2022.9: Enhanced incidents management to improve EDR workflows

Identify sooner. Respond faster
With this month’s update, we’re introducing significant enhancements to our endpoint detection and response (EDR) module, making it easier than ever to identify potential threats and determine which ones should be prioritized.
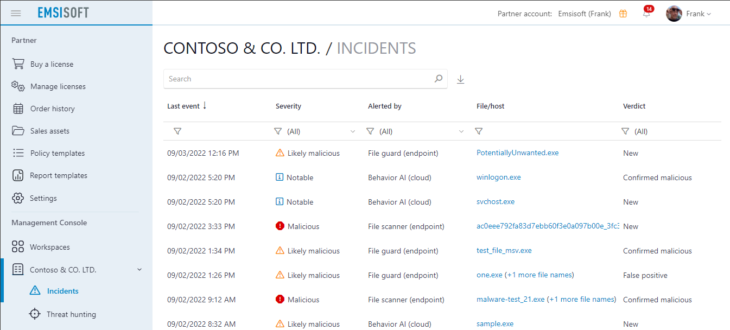
New incidents overview with smart threat severity classification
The ‘Incidents’ panel in your workspace lists all potential threats, both those which were detected locally on endpoints and also those which were detected by Emsisoft’s cloud-based Behavior AI. With this update, the list will be grouped by specific threats, with each entry summarizing all alerts for every file or host, making it quick and easy to get an overview of what’s happened within your environment.
Additionally, the panel now also includes a ‘Severity’ column , with ratings ranging from ‘Malicious’, ‘Likely malicious’, ‘Suspicious’, ‘Notable’ to ‘Unwanted.’ The rating is determined by smart algorithms that take into account the protection layer which detected the threat, a technical analysis of a file, the frequency of specific actions and events, as well as the reputation of a file, and more. The rating helps you quickly hone in the most important items – namely, ‘Malicious’ and ‘Likely Malicious’ detections with are shown in red and orange respectively – and take appropriate action.
Depending on your security requirements, you may want to investigate all alerts on a prioritized basis, or hide certain severity levels from the dashboard completely. The choice is yours. Our objective is to present the information in a way that will enable you to process it in the most time-efficient manner.
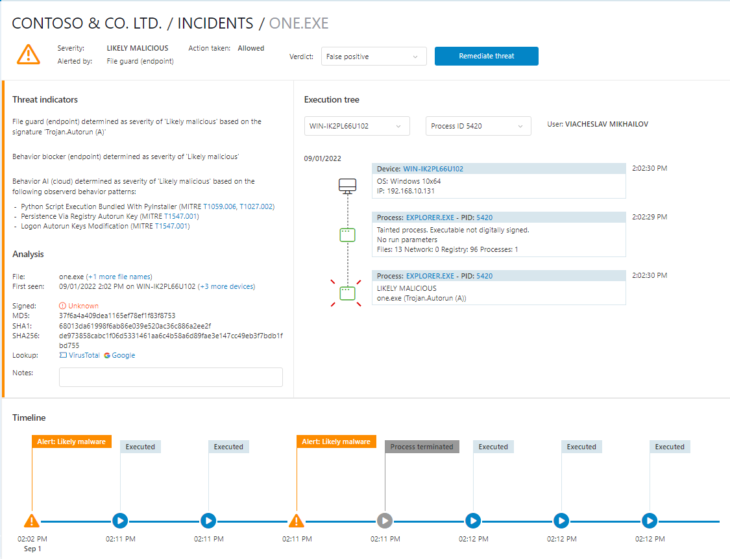
Advanced threat details view with timeline and execution trees
This is the core of Emsisoft’s EDR. We have completely restructured the threat details panel and included a brand new timeline feature which shows all recorded relevant events and alerts.
The panel also lets you jump through all recorded execution trees of a threat on every devices on which it was found. You can use this to trace back to the origins of an attack.
The main purpose of the threat details panel is to help you answer the most important questions:
- What happened? What methods were used and what did the threat aim for in terms of malicious activity? Which behavior types were recorded, including exploiting of vulnerabilities, and potential lateral spread across your devices?
- Where did it happen? Where did the action originate in the network? Which devices were involved and what was the attack vector? For example, did someone open an email attachment, or download and open a file, or was a vulnerability was exploited to execute code?
- Who was responsible? In which user context was the file initially created? That may be a physical user or a system identity.
Emsisoft’s new threat details panel enables you to understand the nature of a threat, contain and remediate it, and take precautions to prevent similar attacks in the future.
Raw data browser
Emsisoft Enterprise Security customers will also notice the new raw data browser at the bottom of the details panel. This shows all related events to a threat, from protection layer alerts, processes, file system and registry activity to networking events. You can drill down on each of the recorded events to find further related activity.
All 2022.9 improvements in a nutshell
Device protection (desktop)
- Fixed issue with high CPU load.
- Fixed issue with firewall status synchronization.
- Removed obsolete scan options that have since been rolled into other protection layers.
- Several minor tweaks and fixes.
Management console (web app)
- New redesigned ‘Incidents’ management panel.
- New ‘Threat details’ panel:
- New timeline.
- Improved execution trees.
- New raw log browser.
- Several minor tweaks and fixes.
How to obtain the new version
So long as you have auto-updates enabled, you will receive the latest version automatically during your regularly scheduled updates.
Note to Enterprise users: If you have chosen to receive “Delayed” updates, client systems will receive the new version no earlier than 30 days after the regular “Stable” availability.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialHave a great and well-protected day!