Gooligan Android malware breaches 1 million Google Play accounts

13,000 devices are infected with Gooligan every day
A new malware attack is hitting Android devices at an alarming rate. This attack is the largest ever breach of Google accounts, according to Check Point, a security research firm that is working with Google to monitor and document the outbreak.
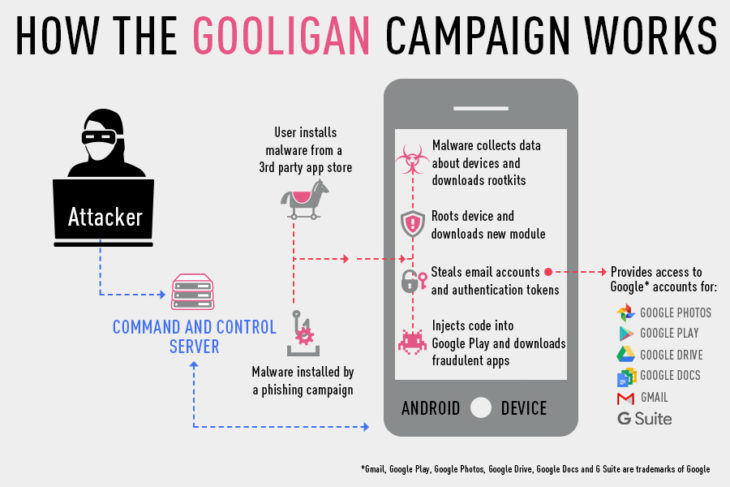
The malware attack hijacks phones using Google authorization tokens and uses them to download unauthorised apps from outside the Google Play store. According to Check Point, which reported the issue to Google, these tokens can be used to access data from Google Play, Gmail, Google Photos, Google Docs, G Suite, and Google Drive. The security company says one million Google accounts have been compromised this way since August, in what it believes is the largest Google account breach to date:
“Gooligan potentially affects devices on Android 4 (Jelly Bean, KitKat) and 5 (Lollipop), which is over 74% of in-market devices today. About 57% of these devices are located in Asia and about 9% are in Europe.”
These apps earn attackers money in two ways:
- Each app install secures a payment for the attacker, while apps also earn revenue from in-app ad services.
- To feed the scheme, the malware also forces infected devices to leave positive reviews and a high rating on Google Play.
Android security lead Adrian Ludwig said in a blog that Google had found no evidence that the user data has been accessed, adding that the main objective of the malware, which is a variant of the already known Ghost Push, is to promote apps rather than steal information.
Google noted in its 2015 annual Android security report that a third of Android apps downloaded outside Google Play were infected with Ghost Push. The malware infected up to 600,000 Android devices per day during its peak.
Gooligan has full access to your private information, regardless of whether they use it to increase ad revenue or steal private information. But what if that access were to end up in the hands of, say, a ransomware developer? Or grant device access to an organisation managing a botnet? Your device’s processing power could easily contribute to the illegal activity of cyber-criminals without you ever knowing. So, how does it gain access?
Gooligan installs malware from 3rd party app stores
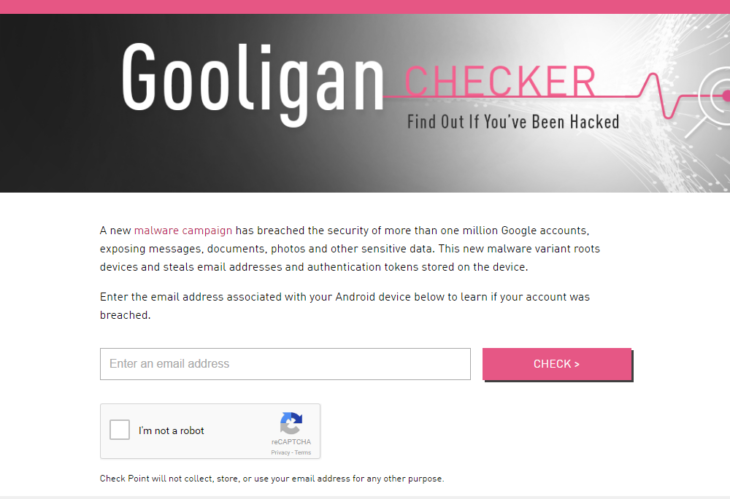
Google releases Gooligan Checker to see if your account has been breached
Check Point has built a ‘Gooligan checker’ where Android users can enter the email associated with their Android device to check if their Google account has been breached. Simply enter your email and instantly receive a pop-up message notifying you if your account is of those known to have been compromised. The company regularly offers patches and similar tools when it uncovers malicious software.
Protection lies in common sense and quality mobile security
The key thing to remember about malware on Android devices is that it has to be installed by you. Malware developers are finding increasingly clever ways to get users to do just that. If an app is asking for access to more than it should reasonably require, such as email, location and full Google access, you should be asking some pretty serious questions about the safety of the app.
Avoid third party app stores. Google does a good job of filtering malware from the original play store.
A quality Android security program is the safety net we need in case of accidental malware download. Emsisoft Mobile Security is an all-round anti-malware with added features such as remote wipe if your phone is stolen and anti-theft which will snap a picture from the front-facing camera if a PIN is entered too many times.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialSafe downloading and have a great (malware-free) day!