Alert: Threat actors are using fake Emsisoft code-signing certificates to disguise their attacks

We recently observed an incident in which a fake code-signing certificate supposedly belonging to Emsisoft was used in an attempt to obfuscate a targeted attack against one of our customers. The organization in question used our products and the attacker’s aim was to get that organization to allow an application the threat actor installed and intended to use by making its detection appear to be a false-positive.
The attack failed – our product detected and blocked it – but we are issuing this alert so that both our customers and users of other company’s products are aware of the tactics that were used in this case.
While the method by which initial access was obtained is unclear, it was most likely via either a brute-force attack on RDP or the use of compromised credentials (a stolen login).
Once the attacker secured access to an endpoint, they installed an open-source remote access application called MeshCentral. This is a dual-purpose application, meaning it is a legitimate tool which can be used for malicious purposes. Because it can be used for legitimate purposes and is not inherently malicious, its presence on an endpoint will not necessarily trigger any alarms, either from security solutions or from humans.
The attacker signed the MeshCentral executable with a certificate called “Emsisoft Server Trusted Network CA”. We believe this was done to make any detection of the application appear to be a false-positive. One of our products was installed and running on the compromised endpoint, after all, so an application that had supposedly been signed by an Emsisoft certificate may be believed to be safe and allow-listed.
As noted above, the attack failed but the incident, nonetheless, highlights the need for organizations to be extremely vigilant when allow-listing. If an organization authorizes an application that should not be allowed, an attacker may be able to disable antivirus protection, move laterally within the network, exfiltrate data, and, ultimately, deploy ransomware.
Users of Emsisoft products can easily check the validity of a certificate used to sign a detected application. If it is verified, it will be marked as “Verified”. If it is not verified, it will be marked as “Unknown”.
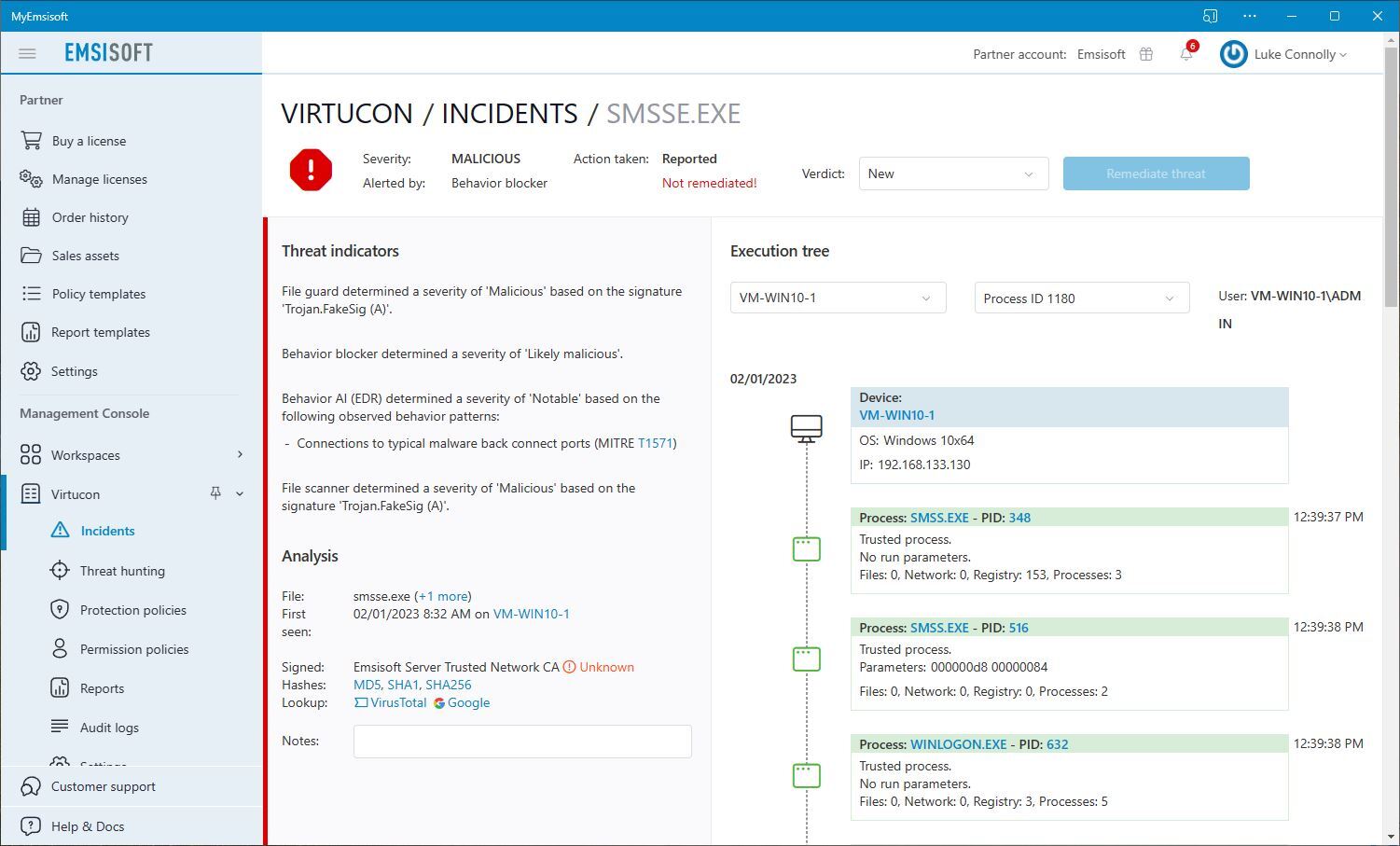
In the case of “Unknown” certificates, the best course of action is to quarantine the application pending further investigation. An application should never be allowed until it is conclusively determined that it is both safe and belongs on the endpoint (in other words, that it was installed by the organization, and not by an attacker). If in doubt, submit the detected application to us for analysis from within your Emsisoft product.
This incident demonstrates the need for organizations to have multiple layers of protection so that, should one layer fail to block an attack, another layer will. It is called the Swiss cheese model, and Emsisoft’s layers include:
- RDP attack detection which will create an alert should an attack be detected. These alerts should always be treated seriously.
- Phishing protection which will help prevent users inadvertently providing their logins to attackers.
- File Guard which uses signatures to detect known threats.
- Behavior Blocking which can determine whether an application is potentially malicious based on its behavioral patterns.
- Set an administrator password on your Emsisoft product. This is anti-tamper mechanism to prevent any attacker who manages to gain access to an endpoint from disabling it.
- Endpoint Detection and Response (EDR) will help suspicious activity to be identified earlier in the attack chain and make root cause analysis quicker and easier.
These and the other layers in Emsisoft’s endpoint protection solutions combine to effectively detect and block threats, no matter the attack vector.
Conclusion
We strongly recommend that users of our products set an administrator password for your Emsisoft product as outlined above. This anti-tamper mechanism ensures that in the unlikely event that a hacker is able to obtain access to an endpoint, they will not be able to disable its protection. This is critically important. Ransomware actors typically attempt to disable security products so that the encryption attempt will not be detected or blocked. Setting a password will ensure they cannot do that. It’s a final line of defense.
Detected applications should only be allowed once it has confirmed to be non-malicious and should be present on the endpoint. If in doubt, seek advice from us or from the vendor of whichever security product you use. Allowing a malicious or dual-use application could enable malware to be installed and result in an incident that is both massively disruptive and extremely expensive.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialIf in any doubt at all, check. We’re here to help.


