How to Perform Manual Ransomware Removal

In the previous two installments of our Malware Removal series, we looked at how to identify and remove unknown malware on a system, and how to remove potentially unwanted programs (PUPs) in particular. In this article, we will take a closer look at a category of malware which has seen a rise in popularity over the last few years: ransomware.
What is ransomware?
Ransomware can be split into two different types; screenlockers and file encryptors.
Screenlockers usually only prevent you from accessing Windows. They demand payment to unlock the system but do not do any actual damage. One particularly popular ruse is to pretend to be law enforcement, claiming they have detected the presence of illegal activities. While cumbersome, recovering from such a ransomware attack is usually quite simple and regaining access to the system is possible.
File encryptors, on the other hand, encrypt personal files or the entire hard drive on a user’s machine, which prevents a user from accessing their files unless they pay the ransom. Not all file-encrypting ransomware uses strong cryptography though, so in many cases, a user can get their data back without paying.
For this blog post, we’ll be focusing on the more common file encryptor type of ransomware. Since ransomware families are constantly changing and evolving, we will demonstrate a typical recovery procedure using an older family of ransomware that turned out to be a true evergreen when it comes to these particular kinds of pests: Xorist.
What to do if you’re infected?
It’s every user’s and administrator’s nightmare: you’ve found yourself infected with ransomware and you’re staring at a message on the screen that demands you pay thousands of dollars to get your files decrypted. What should you do? Don’t panic. A ransomware might present you with a time limit, but it’s important to avoid taking the wrong steps, which could make it harder for you to get your files back.
Step 1: Identify infected machines
First, find the infected computer or computers on your network. This is a really important first step and should be done as soon as you notice that there is a ransomware infection. You can usually locate the computer where the ransomware originated by checking the owner of the ransom note files on the network or file shares. Once you have located the computers which are infected, disconnect them from the network so that the ransomware cannot spread laterally to other computers on the network and prevent the encryption of more files if the ransomware has not already finished.
Step 2: Check if the ransomware is still present
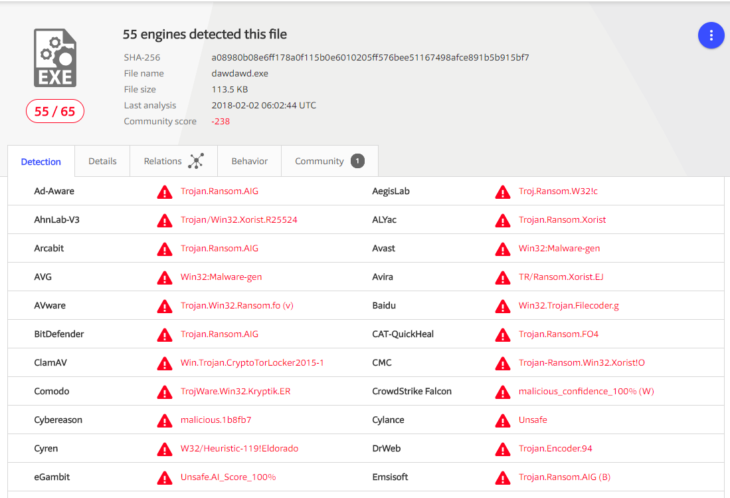
Second, once the infected systems have been disconnected it is important to figure out if the ransomware is still running or present on the system. If so, then it is best to get a process dump of the memory and a copy of the malware before cleaning the system. This is important as the specific ransomware family may still be under analysis. Usually, it is recommended to upload any malicious files to a service called VirusTotal. Powered by antivirus scanners and other security tools from more than 60 different security vendors, VirusTotal can tell you whether a file is clean or provide the detection name if the file is detected as malware.
Step 3: Find out which ransomware you’re dealing with
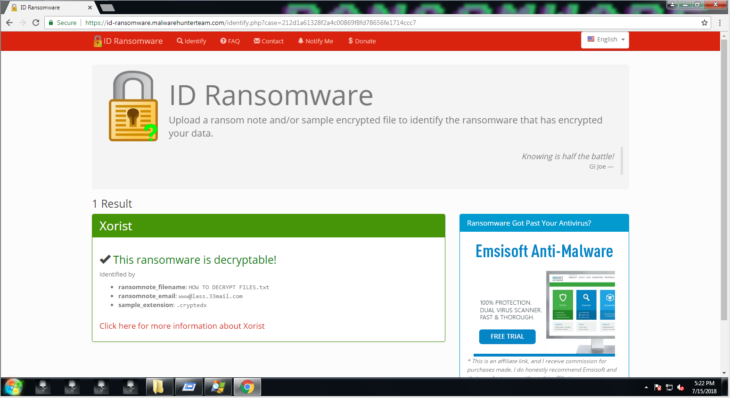
Third, upload a copy of the ransom note and an encrypted file to ID-Ransomware (IDR). IDR is a free service that has been trained to recognize ransomware strains based on clues left behind in encrypted files and ransomware notes. Once you know which strain of ransomware you are dealing with, it is much easier to see if a suitable decrypter is available and if there is information known about how victims are infected.
Step 4: Clean up
Finally, the infected machine needs to be cleaned using the same approach we already outlined in the first installment of our malware removal series.
Deep Dive: How to Remove Xorist
Most of the time manual removal is not necessary. Ransomware often self-deletes as it has already finished the main purpose of encrypting files and dropping a note demanding a ransom. That being said, some ransomware also installs themselves into auto-startup locations to encrypt any new data which was not previously encrypted. Some other ransomware may come with other malware, which can cause further damage.
Since ransomware is constantly evolving, we decided to go with a rather old family that is still very much in use and accounts for a good chunk of all ransomware attacks even years after it was first released: Xorist. While there are certainly more sophisticated ransomware variants out there, most of them haven’t demonstrated the staying power of Xorist.
Xorist is a ransomware construction kit that allows even the most novice cybercriminal to click together a ransomware. Things like background images, ransomware notes, file extensions to be targeted and unlock password are fully customizable. We picked a random variant out of the tens of thousands of Xorist variants attackers have generated over the years.
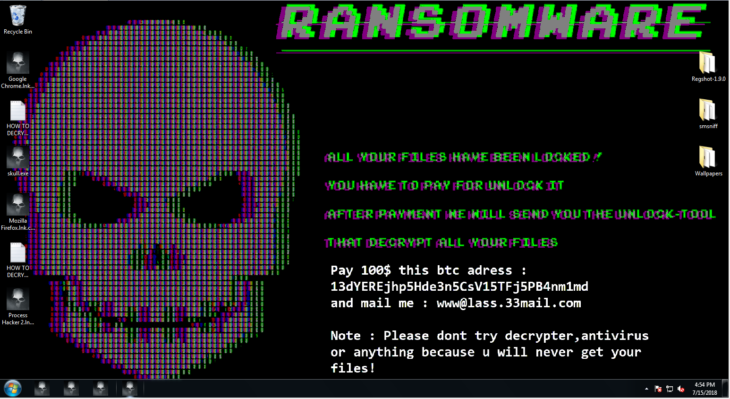
When you first look at an infected system, you will immediately see that the background has been changed to a scary note and all the icons have been changed into skulls.
First of all, we want to check if the ransomware or other malware is still running using Process Explorer or Process Hacker. In this case, the ransomware quit after it finished making changes and no other malware is running. However, if you do find processes running on your machine that look like malware, make sure to create a full process memory dump of them before you suspend or terminate them. To do that, simply right-click the process in the process list and select “Create dump file …” in Process Hacker or “Create Dump/Create Full Dump …” in Process Explorer.
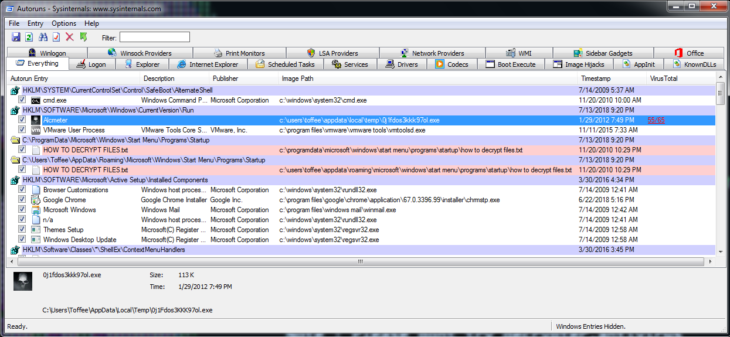
Next, we want to check the load points (how most programs can run at startup) using a handy tool called Autoruns. Once we loaded up Autoruns, we see a value in the Run key with that same skull icon that all our files display now as well. Investigating this further by taking a look at where the file is located (in temp) and by scanning it on VirusTotal (right click and select Submit to VirusTotal), we can determine that this is likely our ransomware file.
One thing to note about scanning files on VirusTotal is that sometimes scanners can have false positives. So if a file has only one or two detections but otherwise looks legitimate it does not necessarily mean that the file is malicious. In that case, it may help to submit the file to us so we can take a closer look.
However, in this case, given the number of detections – along with the icon and the suspicious location – we can assume that this file is malicious and the source of the infection. So, we can either delete the autorun entry by right-clicking the line and selecting “Delete” or we can simply disable it by unchecking the checkbox in front of the entry.
In general, whenever you deal with ransomware, it is a good idea to create a copy of all the malicious executable files you have found. You can simply copy them all into one directory and then ZIP them up. The reason for archiving malicious files instead of just deleting them is quite simple: when dealing with a new ransomware family, companies like ours who help ransomware victims will require the ransomware executable that encrypted the files in order to reverse engineer it and look for flaws in its implementation. Only then will we hopefully be able to turn those flaws into a working decrypter. This process becomes much, much harder if the ransomware executable was deleted by the victim.
After we have disarmed the autorun and archived the ransomware executable, we will submit both the ransom note and one encrypted file to ID-Ransomware. The process is straightforward and most users won’t have any trouble following the instructions on the website. On the off-chance that you find it difficult to use, however, you can check out our step-by-step instructions here.
ID Ransomware correctly identifies the ransomware family for us and already knows which decrypter to use to get our files back.
When dealing with ransomware decrypters, keep in mind that they may not be perfect. A lot of ransomware is shoddily programmed. Some will outright damage parts of the files they encrypt with no way to recover the broken parts. It is best to check the usage information on the decrypter’s download page to figure out if any such restrictions exist and how to use the decrypter properly.
Most decrypters, ours included, will usually require you to have a matching file pair containing one encrypted file as well as its unencrypted, original version. Many victims often don’t know how to get those and think it is impossible to get a matching pair. However, given the following pointers, they usually manage to find a file pair in no time:
- If there are any files encrypted in your Downloads directory, simply download the file again.
- If there are any standard Windows files encrypted, like the default wallpapers for example, simply copy the same files from a different system running the same version of Windows.
- Check your sent emails folder for any files you sent to friends or family that are now encrypted and simply get the original form your sent email.
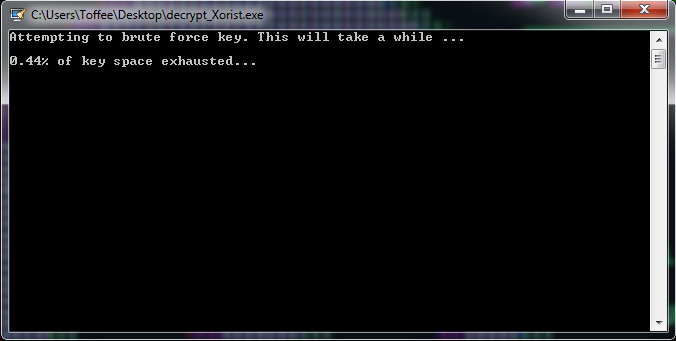
Decrypters will also usually require some time to perform some lengthy computations in order to determine the correct decryption key to use. So please be patient while the decrypter does its job.
Once we have downloaded the Xorist decrypter and run it with a suitable file pair, it will start doing its attack to break the encryption:
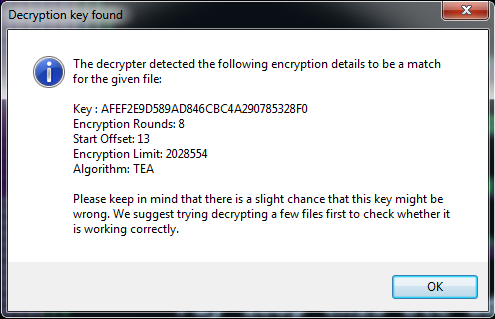
Once it is done, the decrypter will inform us about the results of the process:
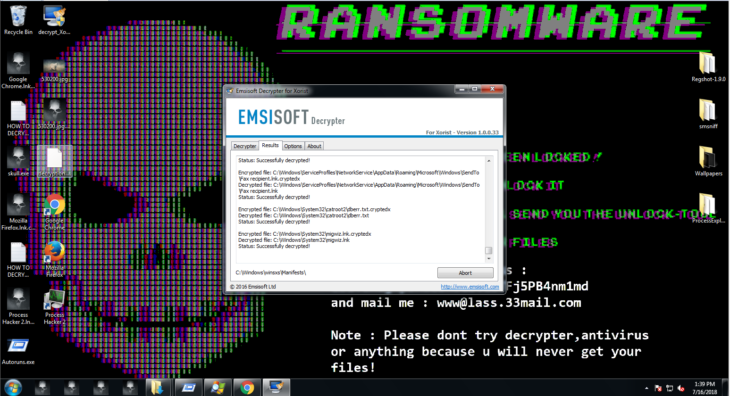
After clicking OK and starting the decryption process, we have our files back:
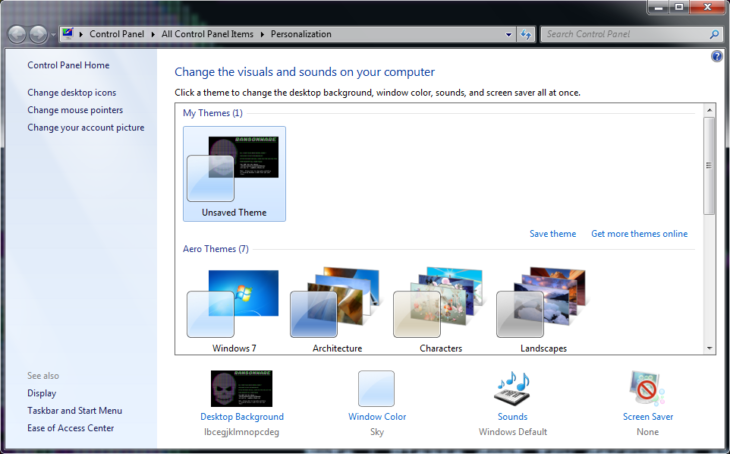
Most ransomware will require some additional cleanup. First of all, the wallpaper. It’s easy to change the wallpaper back using the standard Windows dialog. Simply right-click on an empty space on your Desktop and select “Personalise”. Then change the background back to the one you want:
In this particular case, the ransomware also registered its own file extension (.cryptedx) and linked it up to the ransomware executable. This is why all the encrypted files suddenly had a skull icon. Removing that is a bit more tricky and requires the use of the Windows Registry Editor.
Simply open up the Windows Registry Editor by running the “regedit.exe” command. To get to the “Run” dialog, press the Windows key and the “R” key at the same time.
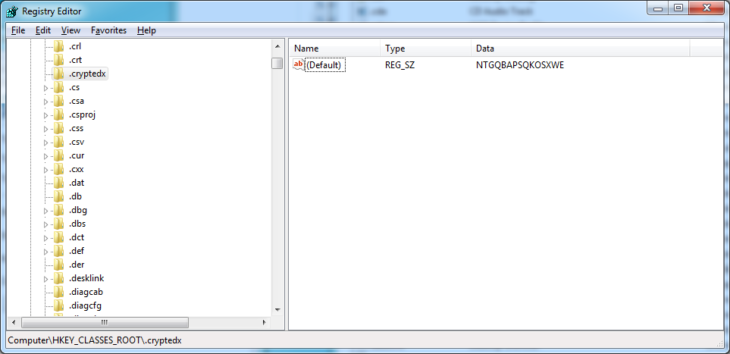
Now navigate to the HKEY_CLASSES_ROOT key. This registry key contains all the links between file extensions as well as the applications they are linked to. Next, look up the sub-key “.cryptedx” inside the HKEY_CLASSES_ROOT key. You will find something similar to this:
There are essentially two ways file extensions can be set up in the registry. Either the information which application to use is stored directly within the file extension sub-key or that information is stored separately and the file extension just links to that other entry. The way to determine which is which is by checking whether or not the file extension key has any sub-keys itself. This is clearly not the case here, as otherwise, it would have a little arrow to unfold its sub-keys in the left-hand navigation pane. So we will take note of the default value (“NTGQBAPSQKOSXWE”) and then delete the key.
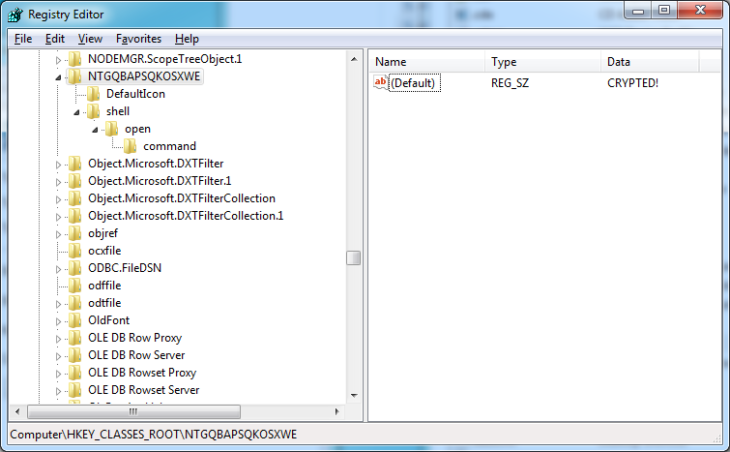
Next, we check out the NTGQBAPSQKOSXWE sub-key. That’s the key that denotes the application to run:
Removing that last key will completely remove the extension registration placed by the malware.
Last but not least, we will have some last bits of cleanup to do. Most decrypters will keep the ransom notes as well as the encrypted files around in case anything goes wrong. After all, having an encrypted backup is still better than having no backups at all. However, once you’ve made sure that you got your files back and they aren’t damaged, they become unnecessary clutter.
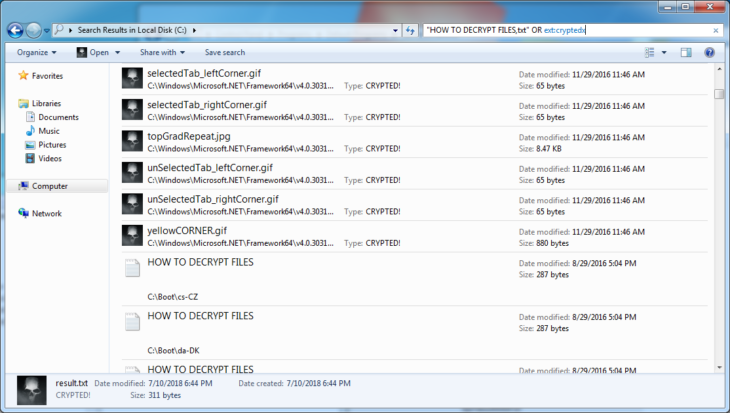
So, in our last step, we use the Windows file search to locate all encrypted files as well as all ransom notes in order to delete them:
Simply select all and delete as you would with any other file and we finished the complete removal of the ransomware infection and the restoration of our files.
Tips on how to avoid ransomware
In a nutshell, ransomware is just ordinary malware. So all the common procedures that are effective against normal malware is just as effective against ransomware, such as:
- Keep your software and operating system up to date to avoid being targeted by exploits and drive-by downloads.
- Don’t engage in high-risk behavior like pirating software or opening email attachments from sources you do not know. Even if you do know the source, use common sense. There is no reason for anyone to wrap an invoice, order confirmation or anything else inside a ZIP archive and send it via email, as most document formats are already compressed. ZIP, in that case, doesn’t reduce the size of the email but is simply used to get past attachment filters that filter out potentially malicious attachments.
- Use a solid antivirus and anti-malware program to help stay protected.
There are a couple of additional steps you can take to stay protected. Backups are the most important one. While backups don’t protect you from getting ransomware, they do help mitigate the damage. The general rule for backups is “3-2-1”. Have 3 copies of your important data. 2 of those copies should not be accessible by your system. And 1 of those copies should be stored off-site. For further details, check out our blog post about the importance of backups as well.
One very common way for cybercriminals to break into servers, in particular, is through deployed remote access tools like RDP or TeamViewer. If you are using any kind of remote access tool on your systems, it is absolutely crucial to stay extra vigilant when it comes to installing security patches. We also recommend using complex passwords and usernames that aren’t easy to guess and can’t be found in existing password dictionaries, otherwise, you will fall victim to a password brute force attack like the thousands of companies who become victims to ransomware every year.
It’s important not to reuse credentials anywhere else as well, as compromises of those systems and platforms may lead to compromises of your system or server. If you can, it is a good idea to restrict access to the remote access ports to only specific IPs or IP ranges. If that’s not an option, changing the port from the default value to something else makes it slightly more difficult for an attacker to figure out you are running remote access software.
Last but not least, we want to clarify once more that when it comes to break-ins via remote access software, no protection software will be able to help you. The reason being is that an attacker can simply uninstall or disable the software before running their ransomware. So it is absolutely crucial that you lock down remote access to your system as tightly as possible and have complex passwords in place.
On-Demand: Manual Ransomware Removal Tutorial

Disclaimer: This article and the webinar are for demonstration purposes only. There are multitudes of ransomware variants in existence and may need a different approach for removal compared to the method presented here, depending on their purpose. We’re aware there are exceptions to every rule and that things aren’t always this straightforward. However, covering all of those exceptions would not serve the purpose of this blog post. If you need assistance in removing malware from your computer, feel free to download our Emsisoft Emergency Kit and reach out directly to our Malware Analysts at [email protected].
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialHave a great (malware-free) day!