Ransomware statistics for 2019: Q2 to Q3 report

Ransomware attacks continued to become more focused and sophisticated in Q2 and Q3 2019. In contrast to the spray-and-pray campaigns of the past, threat actors are increasingly targeting larger and more profitable targets such as businesses, schools and government organizations.
Ransomware strains such as Ryuk played a dominant role, crippling dozens of public entities across the U.S., while ransomware-as-a-service like Sodinokibi and GandCrab enabled ransomware distributors to generate millions, perhaps even billions, of dollars in ransom payments.
This report is based on data from more than 230,000 submissions to Emsisoft and ID Ransomware between April 1 and September 30, 2019. Created by Emsisoft Security Researcher Michael Gillespie, ID Ransomware is a website that enables both businesses and home users identify which ransomware strain has encrypted their files by uploading the ransom note, a sample encrypted file and/or the attacker’s contact information. It also directs the user to a decryption tool, should one be available.
For details on ransomware attacks against U.S. governments, education and healthcare entities, see State of Ransomware in the U.S.: 2019 Report for Q1 to Q3.
What are the most commonly reported ransomware strains?
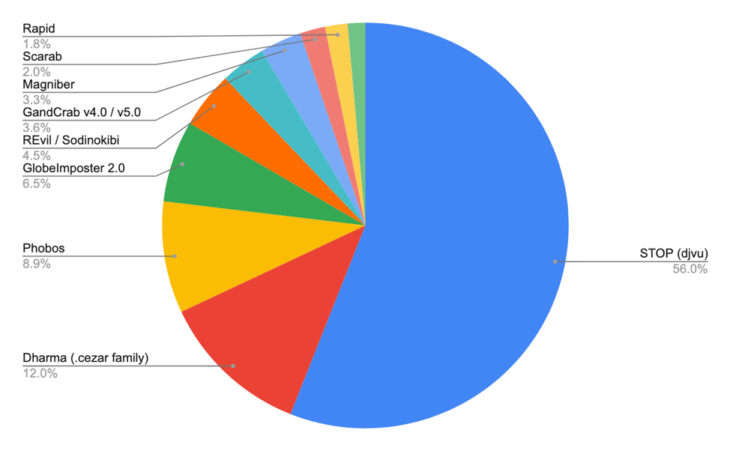
1. STOP (DJVU): 56%
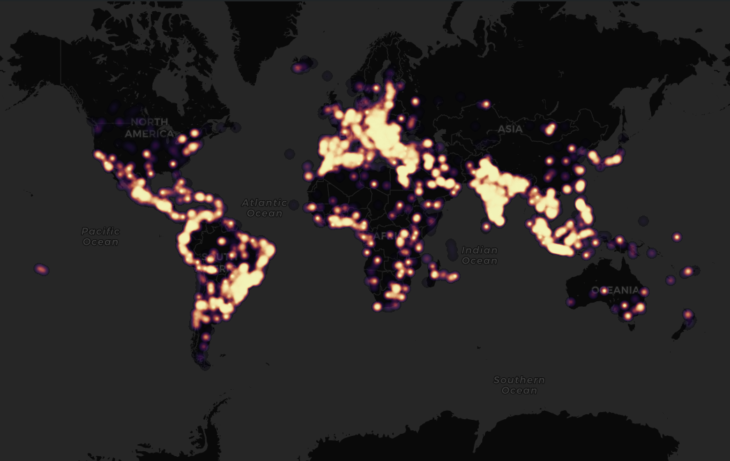
ID Ransomware heatmap for STOP
The most commonly reported ransomware strain during the period April 1 to September 30 was STOP (sometimes referred to as DJVU), which accounted for 56 percent of all submissions. There were more than 76,000 STOP/DJVU submissions to ID Ransomware, which probably represents only a fraction of the total number of victims. First spotted in late 2018, STOP/DJVU has grown to include dozens of variants.
STOP targets home users and is often distributed via torrent sites. It is typically hidden in applications such as software cracks and key generators, which are tools that allow users to activate paid software for free.
Once executed, STOP encrypts files with Salsa20 encryption and instructs the victims to pay a ransom of $490 worth of Bitcoin in exchange for decryptor software and a private decryption key. After 72 hours, the ransom demand doubles to $980. Free decryption tools are available for a limited number of variant, but newer versions cannot be decrypted.
2. Dharma (.cezar family): 12%
The second most common ransomware submitted to ID Ransomware over Q2 and Q3 2019 was a Dharma variant that appends the .cezar extension to encrypted files. It accounted for 12 percent of submissions.
Dharma has been around in one form or another since 2016, but has seen a spike in activity in recent months. This may be due to threat actors making more effective use of multiple attack vectors such as malicious email attachments, infected installers and weak or leaked RDP login credentials. Unlike many other types of ransomware, Dharma (.cezar family) does not specify a ransom amount; instead, it instructs victims to contact the ransomware distributors via email to negotiate the ransom. The ransom amount tends to be higher for larger companies.
Dharma primarily targets businesses. It has affected a number of major organizations, including Altus Baytown Hospital, Texas. The attack encrypted hospital records and files containing important patient information such as names, social security numbers, credit card information and more. The hospital refused to pay the ransom, and instead hired a cybersecurity consultant to restore the hospital’s systems from backups.
3. Phobos: 8.9%
Named after the Greek god of fear, Phobos was responsible for 8.9 percent of ID Ransomware submissions between April 1 and September 30. Phobos closely resembles the Dharma ransomware family and was first spotted in early 2019.
Phobos primarily spreads by exploiting open or poorly secured RDP ports. Lists of stolen RDP credentials are frequently sold on the underground market and can be extremely valuable to cybercriminals. As with Dharma, Phobos does not state a ransom amount and instead instructs victims to email the attackers to discuss the price of decryption. There have been instances of no decryption tool being delivered after payment.
Phobos primarily targets businesses and public entities. In July 2019, the Wyoming Area School District lost access to data after it was hit with Phobos, which entered the system via a brute force attack on an outside port. The school district agreed to pay more than $38,000 worth of Bitcoin to the attackers in order to recover the encrypted files. Most of these costs – as well as additional fees involved with hiring a cybersecurity lawyer and the services of a ransomware recovery company – were covered by the district’s insurer, but the district was still responsible for paying a $10,000 excess.
4. GlobeImposter 2.0: 6.5%
GlobeImposter 2.0 accounted for 6.5 percent of ID Ransomware submissions during Q2 and Q3 2019. Not to be confused with Globe or the original GlobeImposter, GlobeImposter 2.0 uses AES-256 cryptography to encrypt a victim’s files and demands a ransom that ranges from one to 10 Bitcoin.
In June 2019, Auburn Food Bank, a charitable organization that provides free food to people in the Auburn School District, was affected by GlobeImposter 2.0. The ransomware encrypted almost all of the food bank’s computers, preventing staff from accessing their files and emails. Rather than paying the unspecified ransom, Director Debbie Christian opted to wipe all affected systems and rebuild the network. Recovery costs were estimated to be about $8,000.
5. REvil / Sodinokibi: 4.5%
Sodinokibi, sometimes referred to as Sodin or REvil, accounted for 4.5 percent of submissions. First spotted on April 2019, Sodinokibi is believed to have been created by the same group behind the highly profitable ransomware strain known as GandCrab.
Sodinokibi is a ransomware-as-a-service that relies on affiliates to distribute and market the ransomware. It is extremely evasive and uses advanced techniques to avoid being detected by security software. Attack methods include exploitation of a vulnerability in Oracle WebLogic, phishing campaigns and compromised managed service providers (MSPs). Most of the initial Sodinokibi attacks were concentrated in Asia, but more recent outbreaks have targeted European organizations.
Sodinokibi has been involved in several high profile attacks, including a coordinated mass attack on multiple Texas local governments. In August 2019, the Department of Information Resources (DIR) revealed that 22 local entities in Texas had been affected by Sodinokibi, which was deployed through MSP software. A range of important city services were disrupted, such as payment processing operations and the printing of identification documents. The threat actor demanded a ransom of $2.5 million in exchange for the decryption tool – a demand that was rejected by all of the affected entities. Some cities were able to restore their systems from backups, while others were forced to rebuild from scratch. The DIR deployed cybersecurity experts from a number of government agencies to assist with the recovery process.
We developed an imperfect solution for Sodinokibi. It doesn’t completely eliminate the need to pay the ransom, but it can significantly reduce the amount victims have to pay. We used this workaround in a case involving a managed service provider and 1,200 endpoints, and were able to recover the affected systems for approximately 90% less than the initial ransom demand.
Dishonorable mention: Ryuk
Despite not being one of the 10 most commonly submitted ransomware strains, Ryuk deserves a mention due to how disruptive and profitable it was during Q2 and Q3. First seen in August 2018, Ryuk, which is believed to be operated by the cybercrime group Grim Spider, primarily targets large organizations. It is typically distributed via spam email campaigns, or in combination with other types of malware such as Emotet and TrickBot.
Ryuk was involved in a number of high-profile ransomware cases during Q2 and Q3. In May, Ryuk infected the computer systems of Riviera Beach, Florida, after a police department employee opened a malicious email attachment. The city agreed to pay the ransom of almost $600,000 to regain access to utility payment services, and email and phone systems.
A few weeks later Ryuk struck again, this time in Lake City, Florida. City leaders eventually agreed to pay the ransom of $460,000.
Ryuk also affected Collierville, New Bedford and Georgia’s Judicial Council and Administrative Office of the Courts, among many others.
Decryption may be possible in a small number of cases. Our researchers have been able to successfully recover data encrypted by Ryuk in 3-5 percent of cases. Organizations that have been affected by Ryuk can check if their case is decryptable by submitting a sample to Emsisoft or ID Ransomware.
10 most commonly reported ransomware strains
- STOP (djvu): 56.00%
- Dharma (.cezar family): 12.00%
- Phobos: 8.90%
- GlobeImposter 2.0: 6.50%
- REvil / Sodinokibi: 4.50%
- GandCrab v4.0 / v5.0: 3.60%
- Magniber: 3.30%
- Scarab: 2.00%
- Rapid: 1.80%
- Troldesh / Shade: 1.40%
Which countries are most affected by ransomware?
Ransomware is a global concern and Q2 to Q3 2019 was no exception.
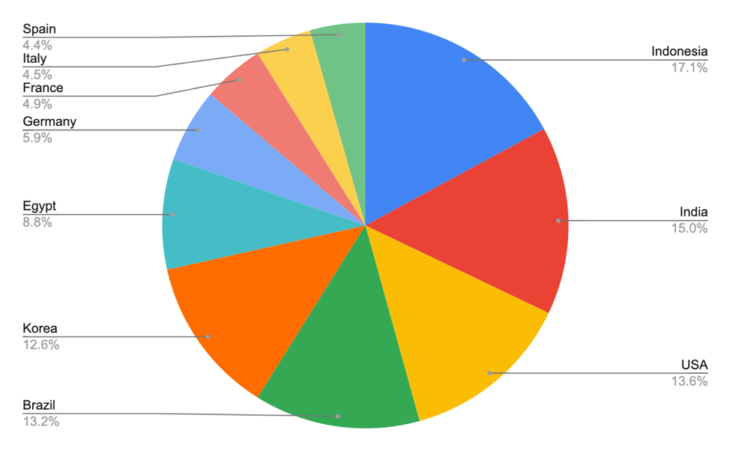
Asian nations proved to be a popular target. Indonesia, for example, accounted for 17.1 percent of submissions, while India was responsible for 15 percent of submissions. This may be explained by the rapid digital expansion in Indonesia and India, which has seen the number of Internet-connected users in these areas rise significantly in recent years. Sudden digital growth can cause a time lag in the adoption of effective cybersecurity measures and consequently leave users more vulnerable to ransomware. In addition, Indonesia has one of the highest rates of software piracy in the world, which may further increase the risk of ransomware infection.
Western nations are also common targets. The U.S., which suffered hundreds of ransomware attacks on local government agencies, schools and public entities over Q2 and Q3 2019, accounted for 13.6 percent of submissions. Meanwhile, Germany, France, Italy and Spain accounted for almost 1 in 5 submissions. Certain types of ransomware, such as Sodinokibi, which are leveraged as ransomware-as-a-service attacks, are often used to demand large ransom sums – sometimes to the tune of hundreds of thousands of dollars. These attacks typically target large companies in the West, presumably because they are perceived to be wealthy and capable of paying the ransom.
Top 10 ransomware submissions by country
- Indonesia: 17.10%
- India: 15.00%
- USA: 13.60%
- Brazil: 13.20%
- Korea: 12.60%
- Egypt: 8.80%
- Germany: 5.90%
- France: 4.90%
- Italy: 4.50%
- Spain: 4.40%
Summary
As ransomware attacks continue to become more sophisticated, organizations need to take a proactive approach to cybersecurity. Businesses of all sizes should review their existing security strategy and ensure their policies and security technologies are in line with current best practices.
In addition to preventative measures, organizations should also have a contingency plan in place in case an infection does occur. Businesses should implement a disaster recovery plan, including a reliable and regularly tested backup system. A robust recovery plan allows organizations to recover their systems without paying a ransom and enables them to resume normal operations as quickly as possible after a ransomware attack.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialOrganizations such as Emsisoft, ID Ransomware and many others are working with law enforcement agencies and anti-ransomware groups such as No More Ransom to help the victims of ransomware recover their files without paying the cybercriminals.