The State of Ransomware in the US: Report and Statistics for Q1 2020
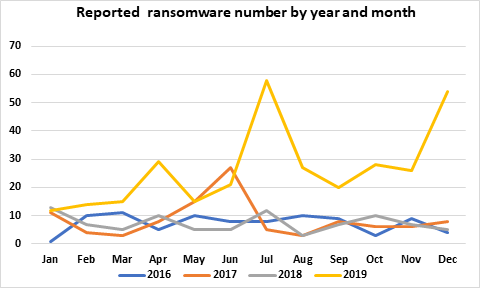
In 2019, 966 government agencies, educational establishments and healthcare providers in the US were impacted by ransomware. While the early indicators were that the 2020 numbers would be similar to 2019’s or perhaps even worse, that has proved not to be the case. A total of 89 organizations were impacted by ransomware in Q1, however, as the COVID-19 crisis worsened, the number of successful attacks reduced considerably and is now at a level not seen in several years.
Government entities
- January – 19
- February – 12
- March – 7
Education
- January – 10
- February – 14
- March – 2
Healthcare
- January – 10
- February – 12
- March – 3
The downward trend is continuing into the second quarter with only a relatively small number of successful attacks having occurred between April 1st and 20th.
- Government entities – 3
- Education – 2
- Healthcare – 2
We believe this marked decrease can be attributed to a combination of factors, including:
- The suspension of non-essential services during the COVID-19 pandemic may have effectively reduced organizations’ attack surface.
- While work from home (WFH) has the potential to introduce security weaknesses, it may, paradoxically, have also created challenges for ransomware groups.
The decline in successful attacks, and especially attacks on healthcare providers, is obviously a positive, but the relief is likely only temporary. Once organizations resume normal operations, we expect the numbers to return to their previous levels.
Breakdown by sector
State, municipal and other government agencies
In Q1, a total of 38 state and municipal agencies were impacted with the number of attacks declining month-over-month. This compares to a total of 113 attacks in 2020 for an average of 28.25 per quarter. Incidents in Q1 included:
- La Salle County, Illinois
- Tillamook County, Oregon
- Colonie, New York
Education
At least 28 universities, colleges and school districts were impacted in Q1, disrupting operations at up to 422 individual schools. In 2019, 89 educational establishments were impacted disrupting operations at up to 1,233 individual schools for an average of 22.25/308.25 per quarter. Incidents in Q1 included:
- Fort Worth Independent School District, Texas
- Gadsden Independent School District, New Mexico
- Spartanburg County School District, South Carolina
Healthcare
In Q1, 25 healthcare providers were impacted compared to a total of 764 in 2019 for an average of 191 per quarter. This reduction is entirely due to the fact that, in 2019, many managed service providers (MSPs) were exploited enabling multiple healthcare organizations to be simultaneously compromised in a single incident. So far in 2020, there have been no such attacks affecting healthcare providers. Incidents in Q1 incidents included:
- Boston Children’s Hospital, Massachusetts
- Jordan Health, New York
- Affordacare, Texas
Insights and observations
While the number of successful attacks on the public sector has decreased, attacks on the private sector have remained largely unchanged during the COVID-19 pandemic, aside from the usual peaks and troughs.
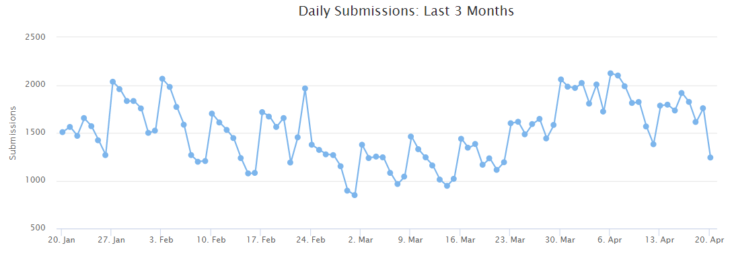
Global daily submissions to ID Ransomware
On a positive note, this means that the predicted surge in attacks has not materialized – which is not surprising. Ransomware groups are limited by their available personnel and infrastructure and cannot rapidly scale up their operations. On a not-so-positive note, it means that a large number of companies continue to be impacted.
A recent report by Chainalysis stated:
The middle of a pandemic is the worst possible time to be hit with a ransomware attack, especially for healthcare providers. So far, the on-chain data suggests ransomware attacks — or, at least, ransomware payments — have decreased significantly since the COVID-19 crisis intensified in the U.S. and Europe in early March.
Given that the number of successful attacks has remained steady, we believe that this reduction is entirely due to the fact that many companies are financially distressed and unable as much they previously did or even pay at all. In a recent note posted to its website, the Maze group stated, “We are living in the same economic reality as you are. That’s why we prefer to work under the arrangements and we are ready for compromise.” That “economic reality” is likely that companies are now less able to pay than they were prior to the COVID-19 outbreak.
Companies are hurting financially and many are reliant on government support programs for their survival. I fully expect that some of the companies hit by ransomware in the coming weeks will fail; attacks will be the straw that broke the camel’s back. — Fabian Wosar, Emsisoft CTO.
Ransomware has a seasonal aspect with the number of successful attacks spiking at certain times of the year.
We anticipate that similar spikes will be seen in 2020 and, consequently, expect to see an increase in the number of successful attacks in the coming weeks.
Conclusion
While the decrease in the number of successful attacks on governments, schools and healthcare providers is certainly welcome, the relief is, as already noted, probably temporary.
The government should, as noted in our 2019 report, seek to bolster security in these sectors and should do so as a matter of urgency. This is critical given that the COVID-19 pandemic could amplify existing security risks around the upcoming election, especially as some states have reallocated election security budgets to fund efforts related to COVID-19.
THANKS AND NOTES
In partnership with Coveware, we’re offering no-cost help to hospitals and other healthcare providers that are on the front lines of COVID-19 and have been impacted by ransomware. Learn more here.
We’d like to thank the academics, journalists, security researchers and other individuals who kindly shared information with us. Without that information, we would not have been able to help as many ransomware victims as we did. We hope the information we were able to share with them was equally useful.
This report is based on data from multiple sources, both public and non-public, and may understate the actual number of incidents.