Ransomware Profile: Mespinoza / PYSA

Mespinoza, sometimes referred to as PYSA, is a ransomware variant that primarily targets large organizations with high-value data assets. It is one of the few strains that target both Windows and Linux systems. Due to severe flaws in the Mespinoza decryptor, there is a significant risk of data corruption occurring when using the attacker-provided decryptor.
What is Mespinoza?
Mespinoza is a strain of ransomware that encrypts files and demands a large ransom for their decryption. Mespinoza is sometimes referred to as PYSA due to the .pysa file extension that new versions of the ransomware append to encrypted files.
Mespinoza is categorized as ransomware-as-a-service (RaaS), a business model used by ransomware developers in which the ransomware is leased to affiliates who can earn a portion of ransom payments in exchange for infecting systems.
Like many other ransomware groups, Mespinoza uses data exfiltration as a conversion tactic to pressure victims into paying the ransom. If the victim refuses to pay the ransom, the stolen data may then be published on Mespinoza’s leak site or sold.
Paying attackers does not guarantee safe data recovery
With any attacker-provided decryptor, there is a risk that data may be damaged during the decryption process. With Mespinoza, the risk is particularly pronounced due to the way the decryptor handles block ciphers (an encryption method that operates on blocks of data of a fixed size – in this case, 16 bytes). As a result, files may not open or may contain missing or incorrect data once they have been decrypted.
It is also important to note that paying the ransom does not guarantee the non-release of exfiltrated data. We have seen confirmed instances of Mespinoza leaking stolen data even after the victim company has paid the ransom. For these reasons, organizations that have been impacted by Mespinoza should be extremely wary of co-operating with attackers.
Emsisoft’s decryption tool can safely decrypt data encrypted by Mespinoza, provided the victim has obtained the decryption keys. The tool can also identify which data has been corrupted and can no longer be trusted. Mespinoza’s decryptor does not have the capability to identify damaged data.
The history of Mespinoza
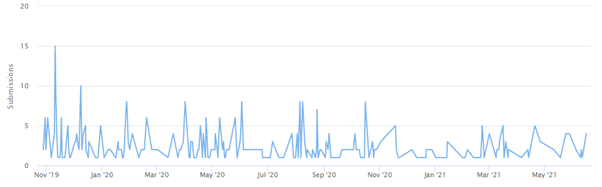
Mespinoza was first observed in October 2019. It originally appended the .locked extension to encrypted files before shifting to using the .pysa extension in December 2019. The developers of Mespinoza have rewritten the malware several times since its release, including a .NET, C++ and Python version, each with its own quirks that can potentially damage data during decryption.
Since Mespinoza was first discovered, there have been 531 submissions to ID Ransomware, an online tool that helps the victims of ransomware identify which ransomware has encrypted their files. We estimate that only 25 percent of victims make a submission to ID Ransomware, which means there may have been a total of 2,124 Mespinoza incidents since the ransomware’s inception. During this time, the group has also published on its leak site the stolen data of at least 104 organizations.
In March 2020, the French National Agency for the Security of Information Systems issued an alert warning of a spike of Mespinoza attacks on the networks of local French government authorities.
In March 2021, the FBI issued a similar alert following a surge of Mespinoza attacks in the education sector. The alert stated that the group had targeted higher education, K-12 schools and seminaries in 12 U.S. states and the United Kingdom.
Mespinoza ransom note
After encrypting data on the compromised system, Mespinoza drops a note called Readme.README.txt in all infected directories. The note contains instructions on how to contact the attackers and threatens that the victim’s data will be leaked or sold in the event of non-payment. The ransomware also adds a reference to the system registry to display the ransom note every time the device is booted.
Below is a sample Mespinoza ransom note:
Hi Company,
Every byte on any types of your devices was encrypted.
Don’t try to use backups because it were encrypted too.
To get all your data back contact us:
[REDACTED]
[REDACTED]
Also, be aware that we downloaded files from your servers and in case of non-payment we will be forced to upload them on our website, and if necessary, we will sell them on the darknet.
Check out our website, we just posted there new updates for our partners: [REDACTED]
————–
FAQ:
1.
Q: How can I make sure you don’t fooling me?
A: You can send us 2 files (max 2mb).
2.
Q: What to do to get all data back?
A: Don’t restart the computer, don’t move files and write us.
3.
Q: What to tell my boss?
A: Protect Your System Amigo.
Who does Mespinoza target?
Mespinoza is big-game ransomware that primarily targets large organizations that are especially sensitive to data loss and/or system downtime. This includes organizations in the healthcare, government and education sectors, as well as private businesses across multiple verticals. Mespinoza is one of a handful of ransomware groups that attacks both Windows and Linux systems.
How does Mespinoza spread?
Threat actors typically gain access to the target network via compromised remote desktop protocol credentials or phishing emails. After the network has been compromised, attackers use open source tools like Advanced Port Scanner and Advanced IP Scanner to perform network reconnaissance, and establish a stronger foothold through the use of tools like PowerShell Empire, Koadic and Mimikatz. Unlike some other ransomware families, Mespinoza does not delete shadow copies before decryption.
Prior to encryption, attackers exfiltrate files from the victim’s network using tools such as WinSCP. Stolen data may also be uploaded to MEGA.NZ, cloud storage and file sharing service, either by uploading the data through the MEGA website or by installing the MEGA client on a compromised endpoint.
Threat actors then deploy the ransomware, which encrypts most files on the system using RSA-4096 and AES-256-CFB encryption. The ransomware does not encrypt crucial operating systems files that are necessary for the victim to process the ransom payment and decrypt data.
As Mespinoza operates as a RaaS and can be distributed by many different affiliates, the exact anatomy of an attack can vary from incident to incident.
Major Mespinoza attacks
- MyBudget: In May 2020, Australian money management firm MyBudget suffered a Mespinoza attack, resulting in 13 days of downtime. Stolen data was initially posted on Mespinoza’s leak site before being removed the following month, leading some to speculate that the company may have paid the ransom.
- Hackney Council: In October 2020, Hackney London Borough Council was infected with Mespinoza. The attack impacted a number of government services, including systems that allowed residents to pay rent and council tax, access housing benefit payments and process land requests. In January 2021, Mespinoza published on its leak site a large amount of data exfiltrated during the attack, including passport details, staff information and photo IDs.
- Sierra College: In May 2021, Sierra College, California, was hit by Mesnipoza. As a result of the attack, Sierra College temporarily lost access to its learning management system, and the college’s main website and payroll systems were knocked offline.
How to protect the network from Mespinoza and other ransomware
The following practices may help organizations reduce the risk of a Mespinoza incident.
- Cybersecurity awareness training: Because the majority of ransomware spreads through user-initiated actions, organizations should implement training initiatives that focus on teaching end-users the fundamentals of cybersecurity. Ransomware and propagation methods are constantly evolving, so training must be an ongoing process to ensure end-users are across current threats.
- Credential hygiene: Practicing good credential hygiene can help prevent brute force attacks, mitigate the effects of credential theft and reduce the risk of unauthorized network access.
- Multi-factor authentication: MFA provides an extra layer of security that can help prevent unauthorized access to accounts, tools, systems and data repositories. Organizations should consider enabling MFA wherever possible.
- Security patches: Organizations of all sizes should have a robust patch management strategy that ensures security updates on all endpoints, servers, and appliances are applied as soon as possible to minimize the window of opportunity for an attack.
- Backups: Backups are one of the most effective ways of mitigating the effects of a ransomware incident. Many strains of ransomware can spread laterally across the network and encrypt locally stored backups, so organizations should use a mixture of media storage, and store backup copies both on- and off-site. See this guide for more information on creating ransomware-proof backups.
- System hardening: Hardening networks, servers, operating systems and applications is crucial for reducing the attack surface and managing potential security vulnerabilities. Disabling unneeded and potentially exploitable services such as PowerShell, RDP, Windows Script Host, Microsoft Office macros, etc. reduces the risk of initial infection while implementing the principle of least privilege can help prevent lateral movement.
- Block macros: Many ransomware families are delivered via macro-embedded Microsoft Office or PDF documents. Organizations should review their use of macros, consider blocking all macros from the Internet, and only allow vetted and approved macros to execute from trusted locations.
- Email authentication: Organizations can use a variety of email authentication techniques such as Sender Policy Framework, DomainKeys Identified Mail, and Domain-Based Message Authentication, Reporting and Conformance to detect email spoofing and identify suspicious messages.
- Network segregation: Effective network segregation helps contain incidents, prevents the spread of malware and reduces disruption to the wider business.
- Network monitoring: Organizations of all sizes must have systems in place to monitor possible data exfiltration channels and respond immediately to suspicious activity.
- Penetration testing: Penetration testing can be useful for revealing vulnerabilities in IT infrastructure and employees’ susceptibility to ransomware. Results of the test can be used to allocate IT resources and inform future cybersecurity decisions.
- Incident response plan: Organizations should have a comprehensive incident response plan in place that details exactly what to do in the event of infection. A swift response can help prevent malware from spreading, minimize disruption and ensure the incident is remediated as efficiently as possible.
How to remove Mespinoza and other ransomware
Mespinoza uses encryption methods that currently make it impossible to decrypt data without paying for an attacker-supplied decryption tool.
Victims of Mespinoza should be prepared to restore their systems from backups, using processes that should be defined in the organization’s incident response plan. The following actions are recommended:
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trial- Take action to contain the threat.
- Determine the extent of the infection.
- Identify the source of the infection.
- Collect evidence.
- Restore the system from backups.
- Ensure all devices on the network are clean.
- Perform a comprehensive forensic analysis to determine the attack vector, the scope of the incident and the extent of data exfiltration.
- Identify and strengthen vulnerabilities to reduce the risk of a repeat incident.